This article helps you change the following items if your cloud provider didn't do that for you.
- Rename server, (optional) join AD domain.
- Create your own account instead of Administrator.
- Disable Administrator login.
- Change remote desktop default port.
- Disable IIS dangerous protocol.
- Install some very infrastructure tools.
After you buying a Windows Server from some cloud provider, or just installed a new server with CD\DVD, you may have a default Administrator user. You may use that user, but it's very dangerous. Here is why:
- Administrator is a name easy for hackers to guess because it is just the default user name.
- When the Administrator is running some program with UAC, it will NOT show any warning message like this, but the app directly get admin privilege. So it's possible that your system running some ransomware.
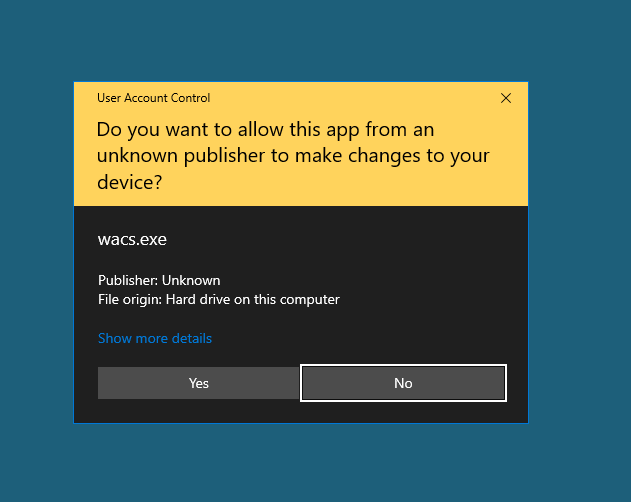
Here are steps which you should follow:
First, sign in your Windows Server:
Go to the machine's property:
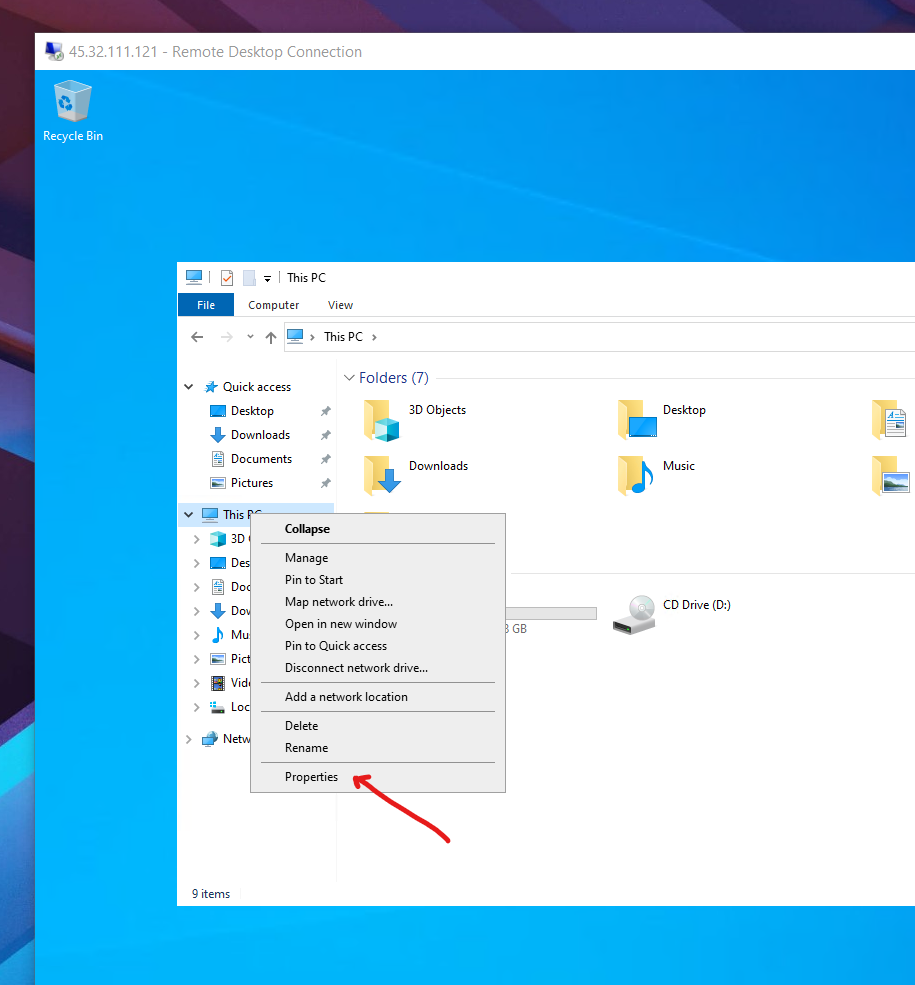
Click rename the PC.
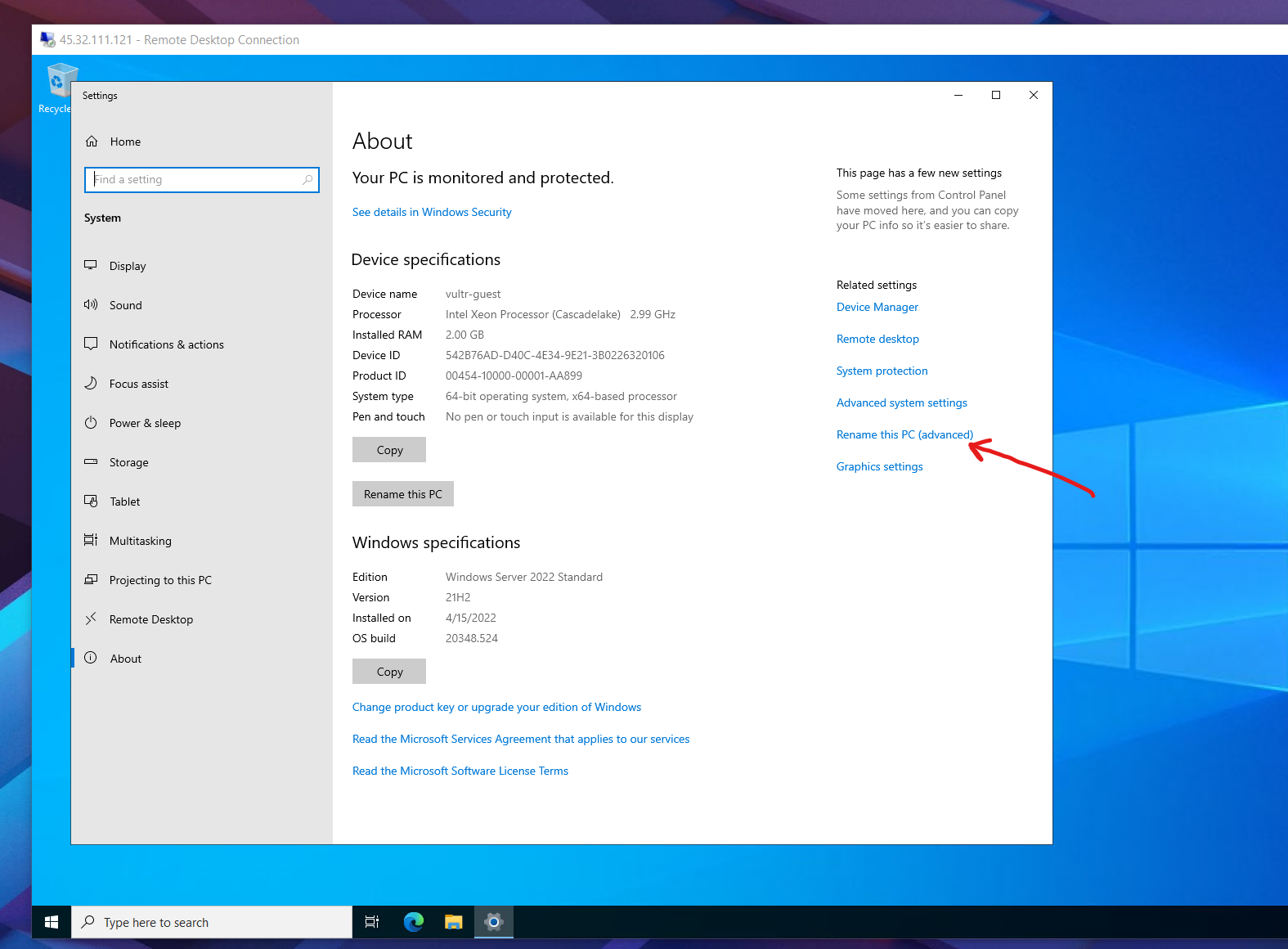
Name the server to the name which describes it's feature. Like 'Web' server or 'Database' server.
Join the Active Directory domain if you have. Or just leave it in workgroup.
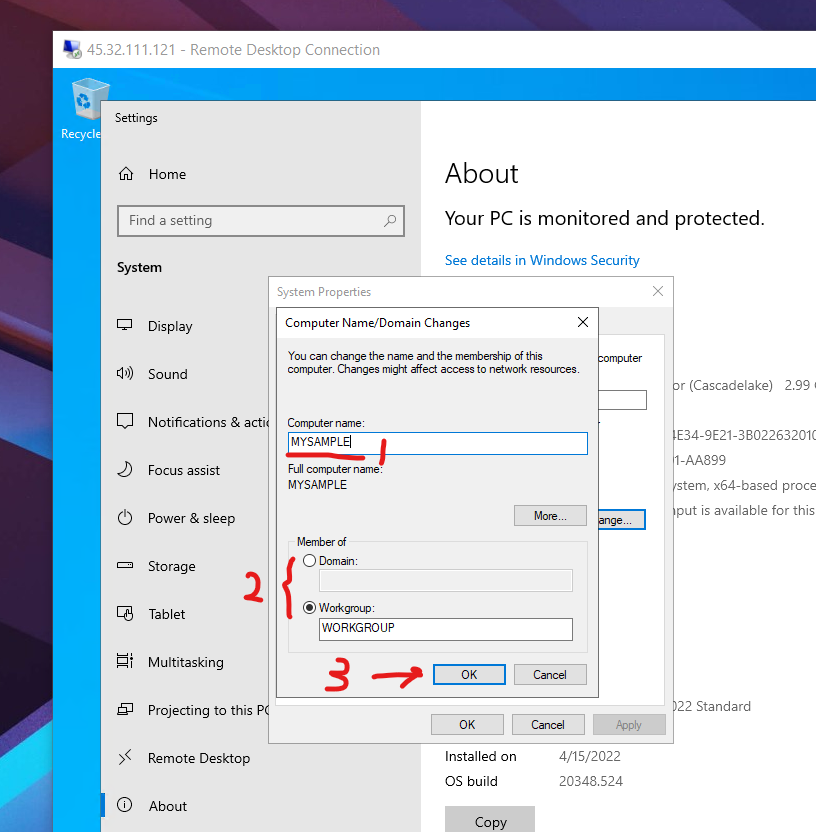
Click Ok. And reboot.
After rebooting, go to the computer management.
Then create a new user:
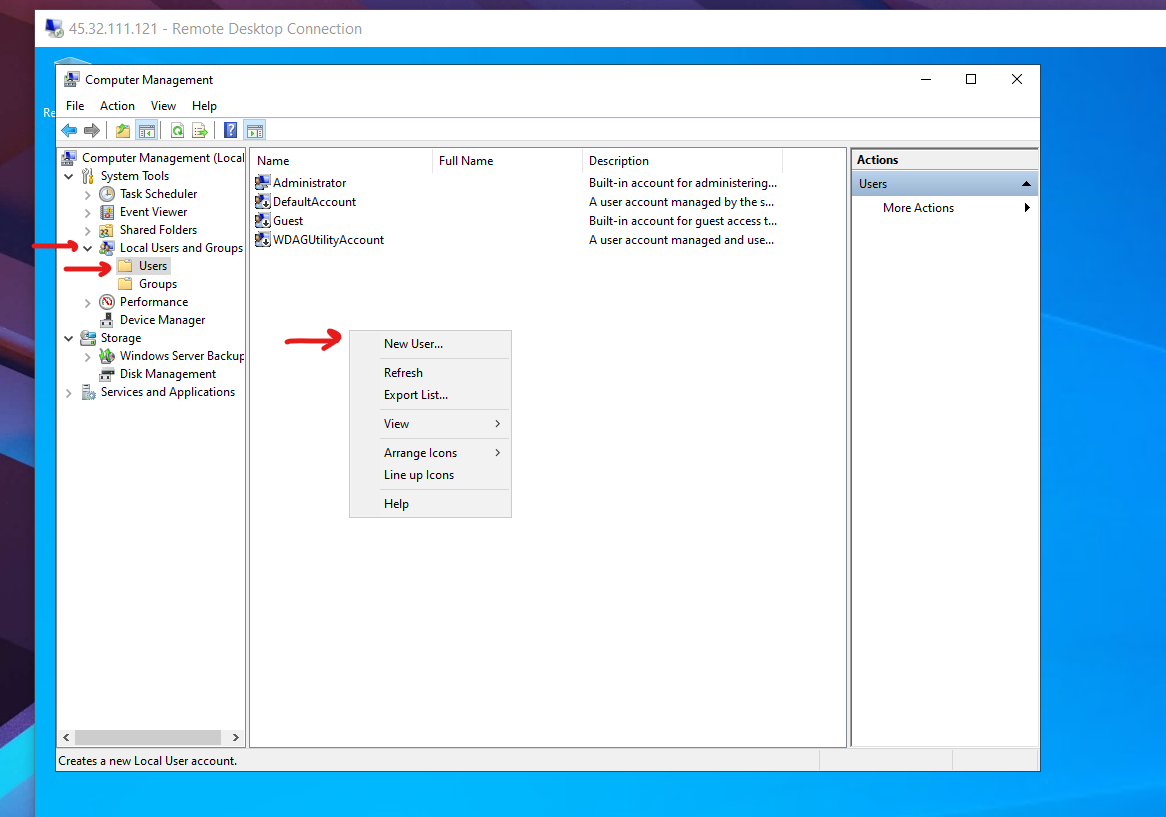
Type your name and create a strong password. Then create the user.
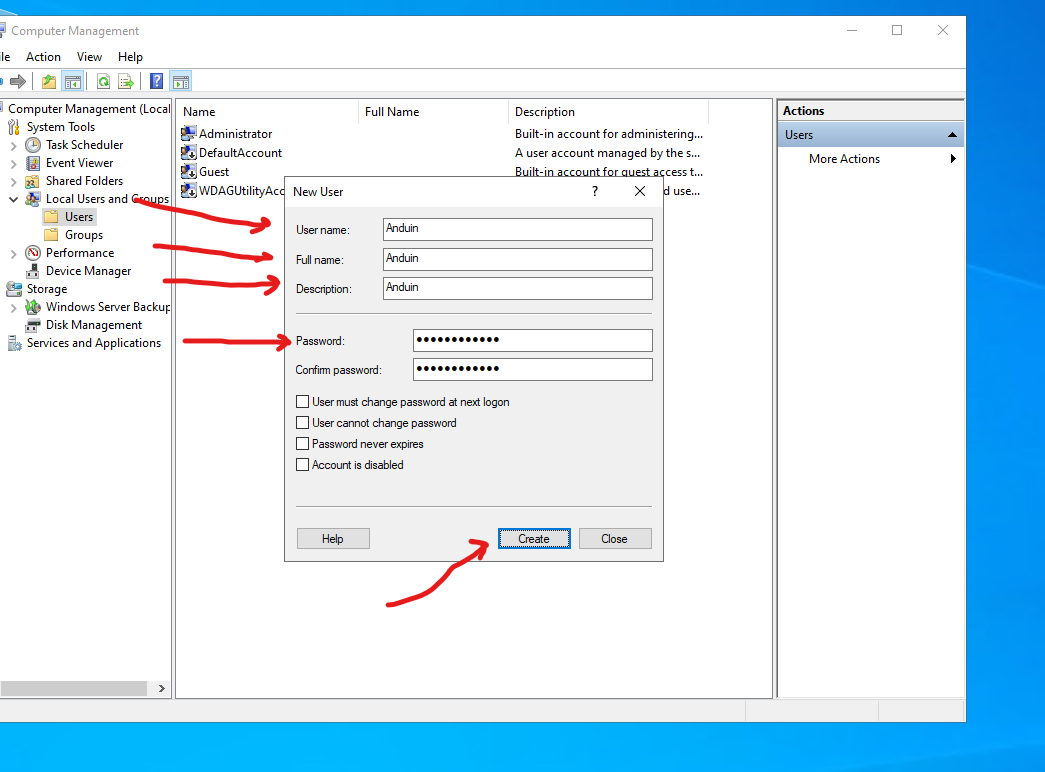
After creating, add the user to Administrators group.
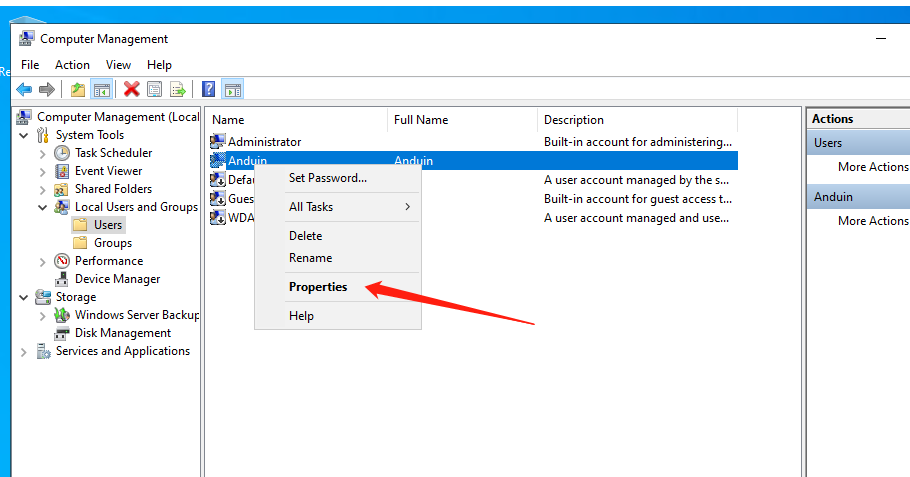
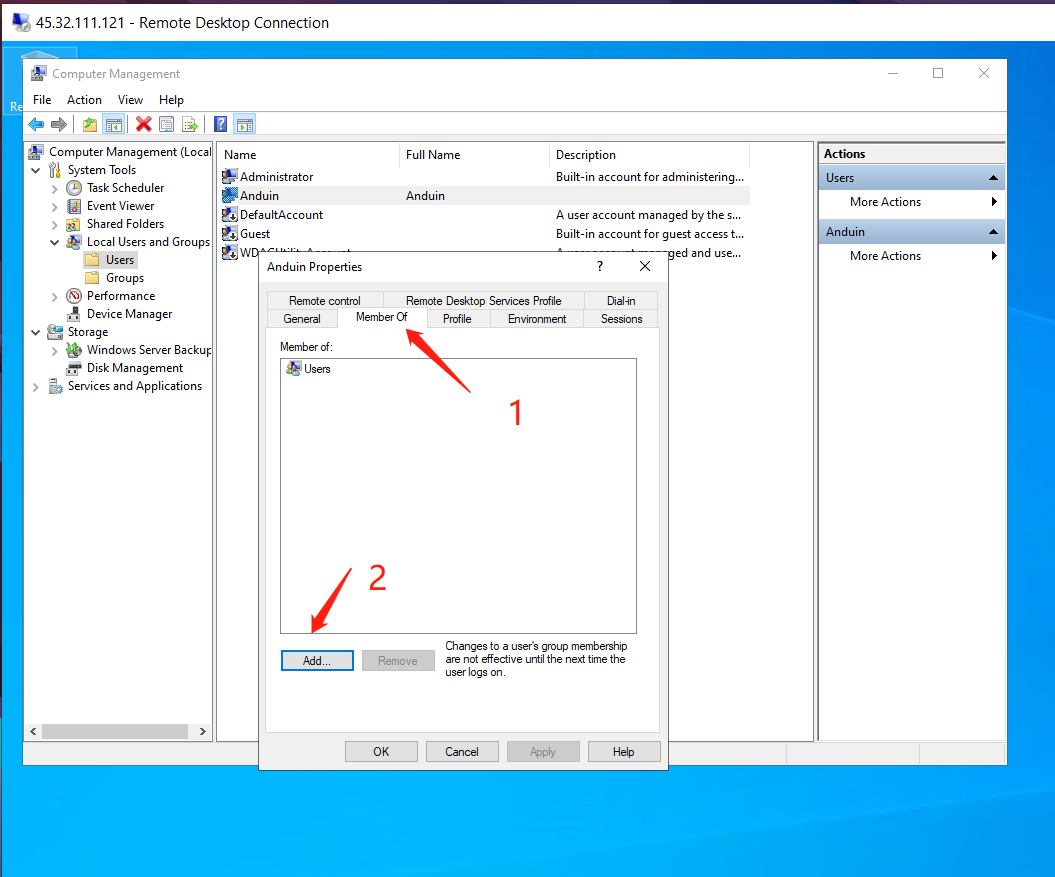
Add the new user to Administrators group.
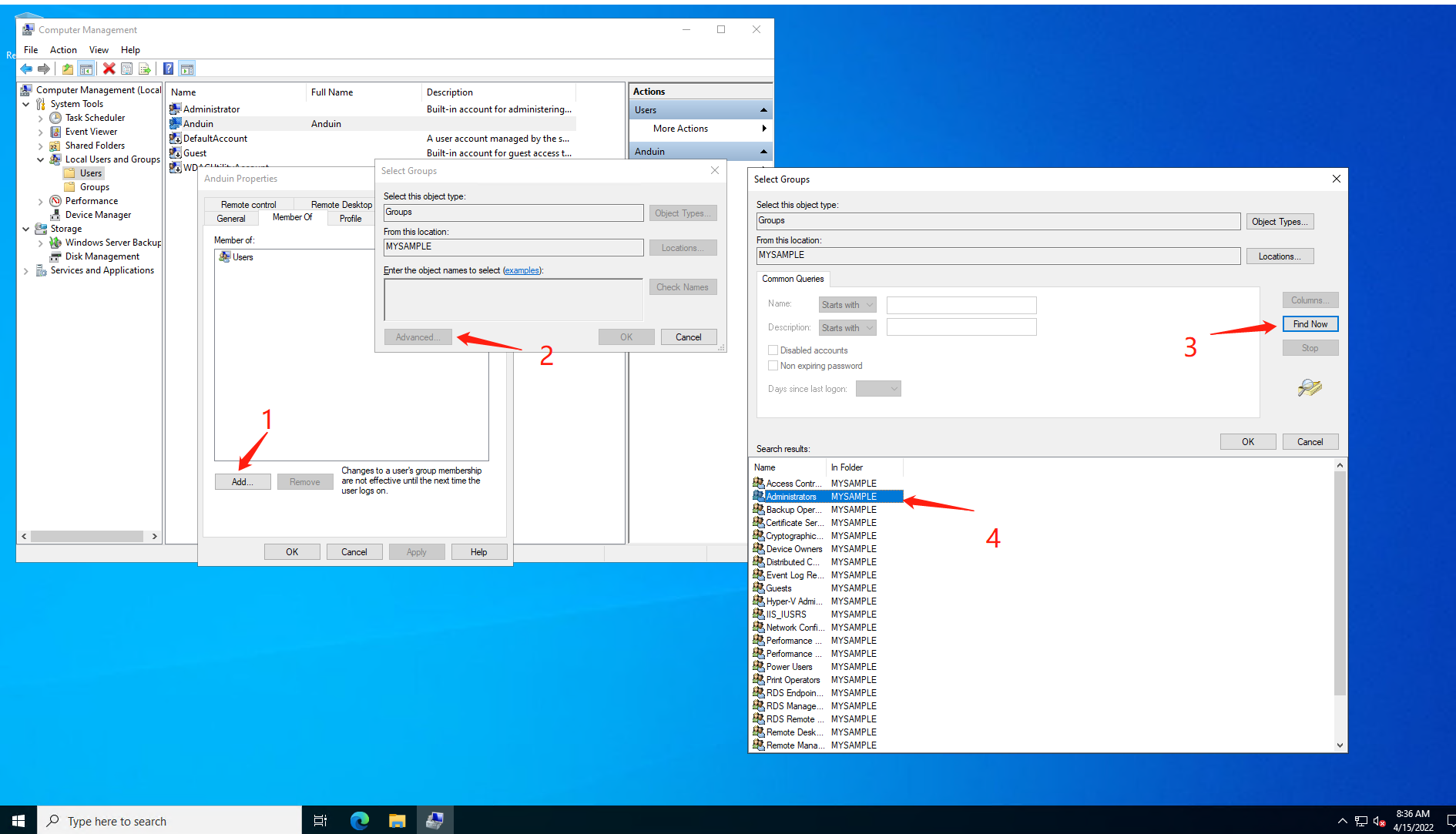
And then sign out the Administrator.
Connect to the server again. This time, use your own account instead of Administrator:
After signing in, test the privilege of your new user:
You may see this:
Click Yes. And type 'whoami' to verify that it's you.
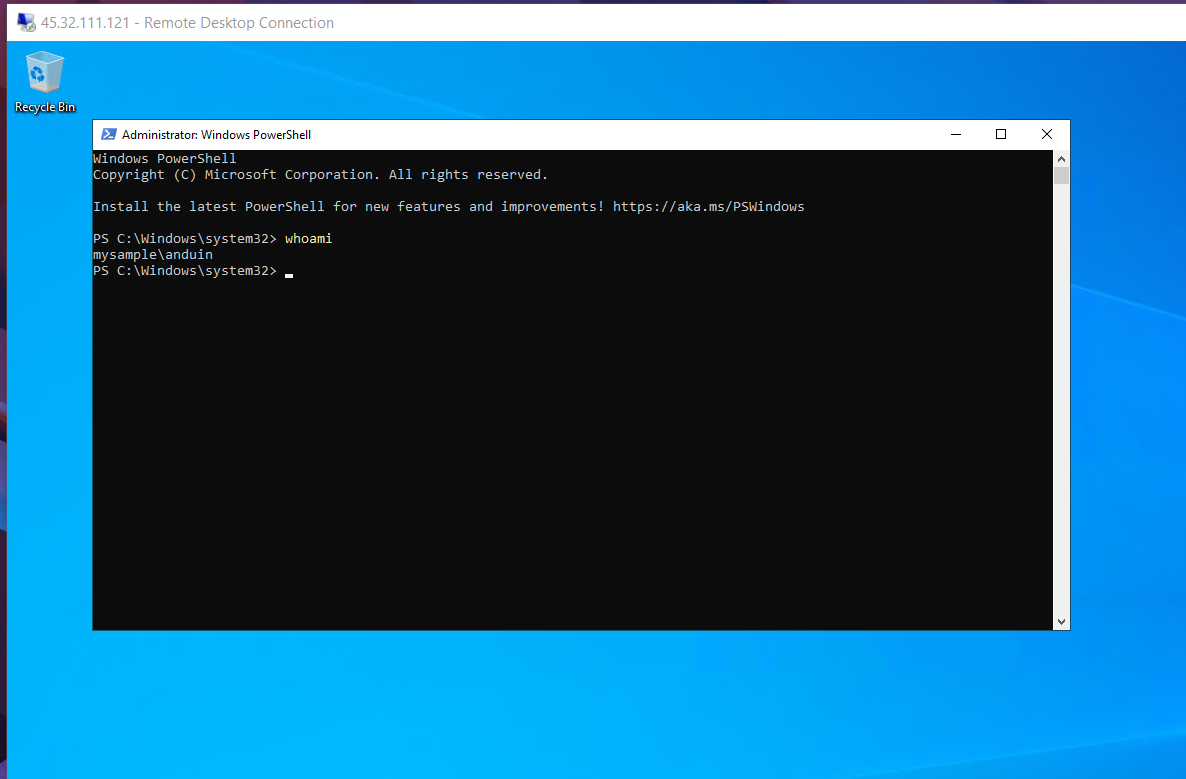
Then we need to disable the default Administrator user. This might be dangerous because if Administrator is the only user in Administrators group, you won't be able to add it again. That's why we did a verification first.
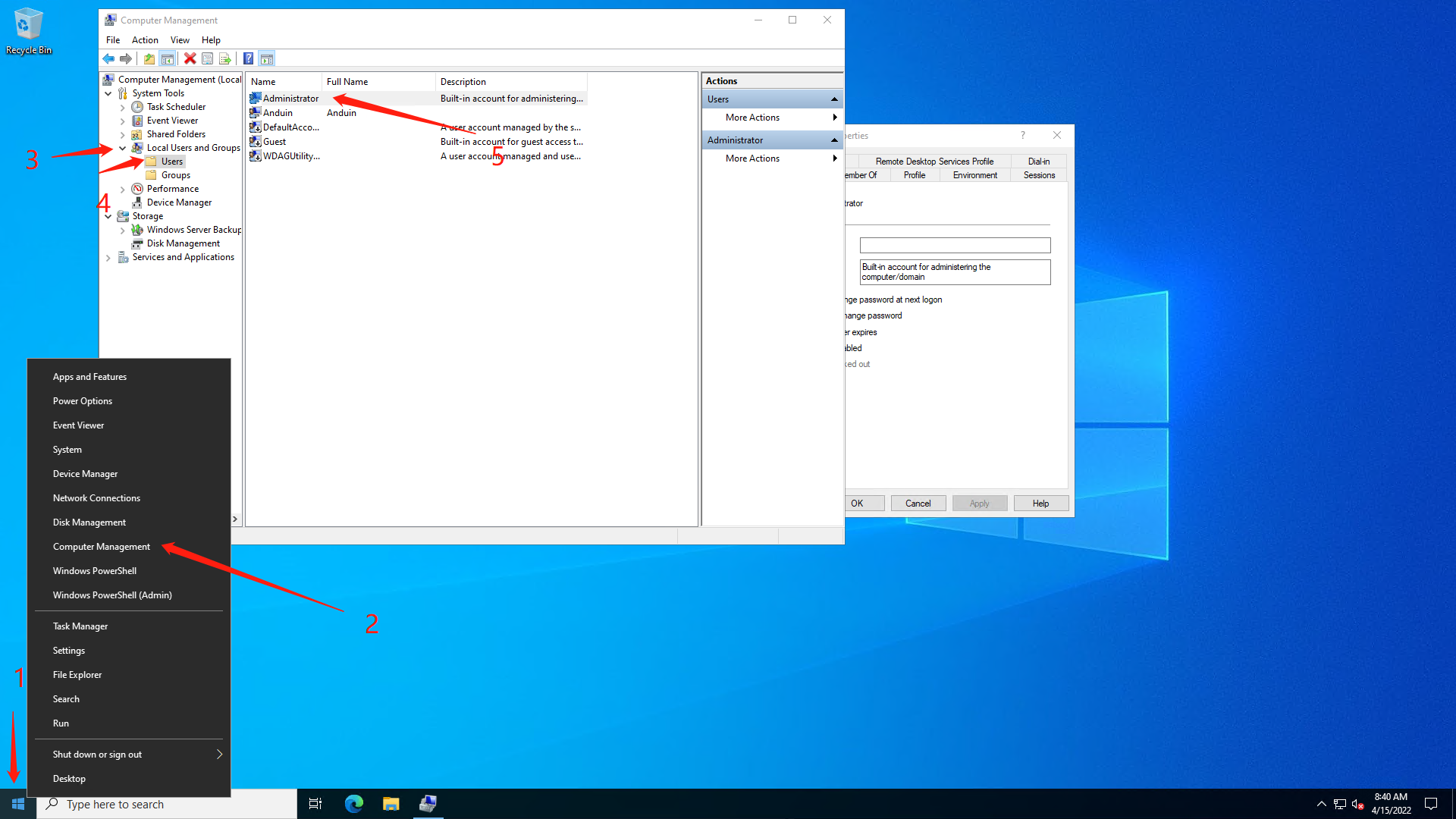
In the properties of the Administrator user, disable it. So no one can use that account again.
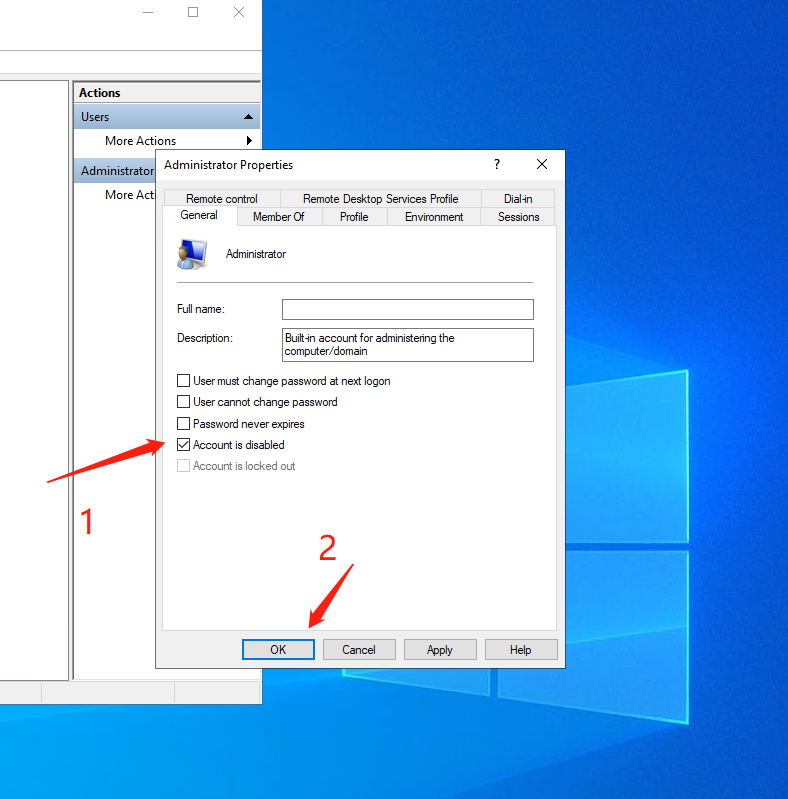
Now we need to change the default RDP port. It's 3389 by default. But it is reported that there are a lot of crackers group attempting to brute force the passwords of all machines with port 3389 open.
If you change that port away to other values, like 33890, it's hard for them to guess. Remote connecting to your computer means that he needs to know:
- Port
- Username
- Password
Click Windows + R to open the Run dialog box. Run 'regedit' and click Ok.
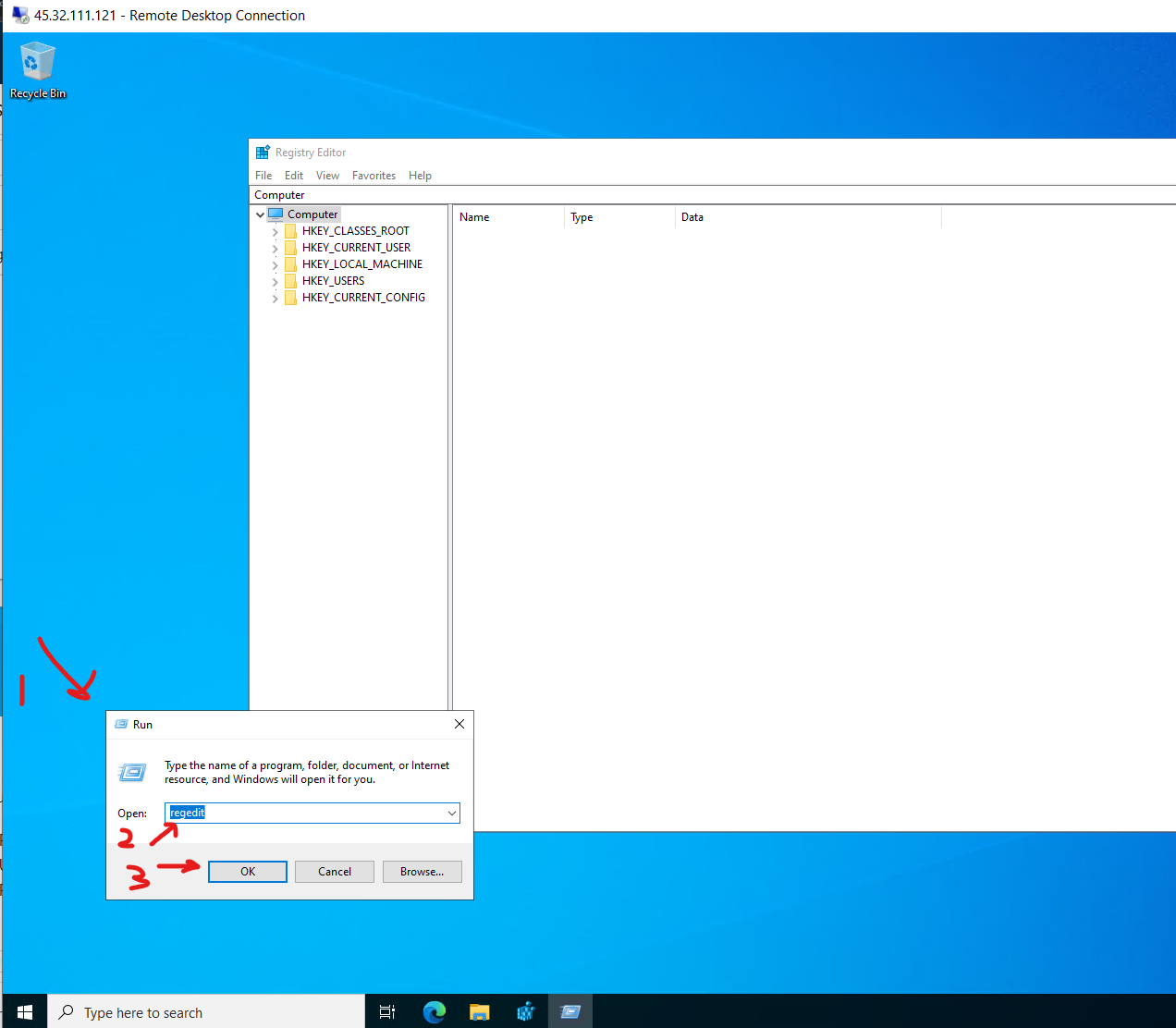
Then navigate to:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
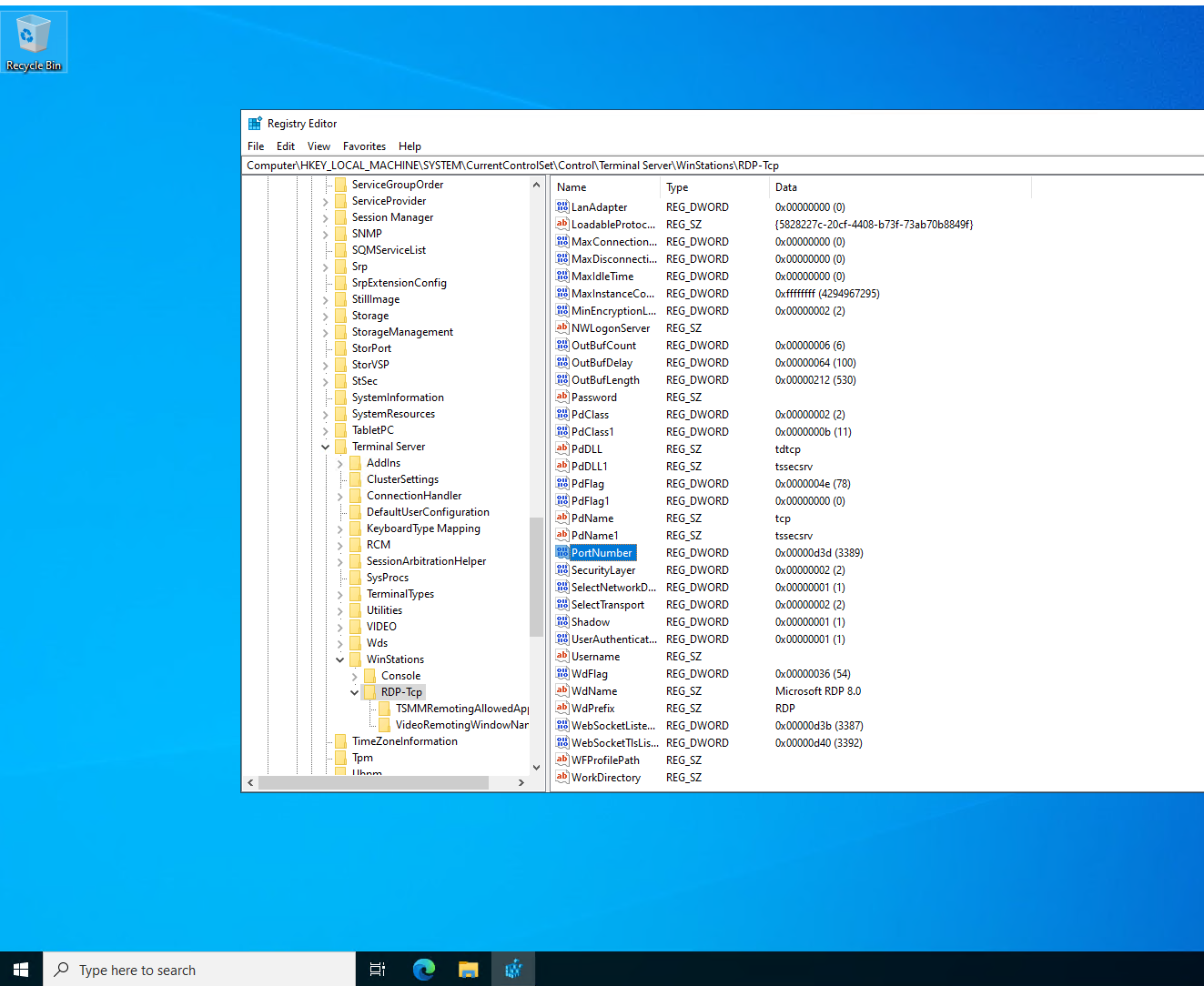
Change that number away to 3390-65535. Pick your own. I use 33890 as an example:
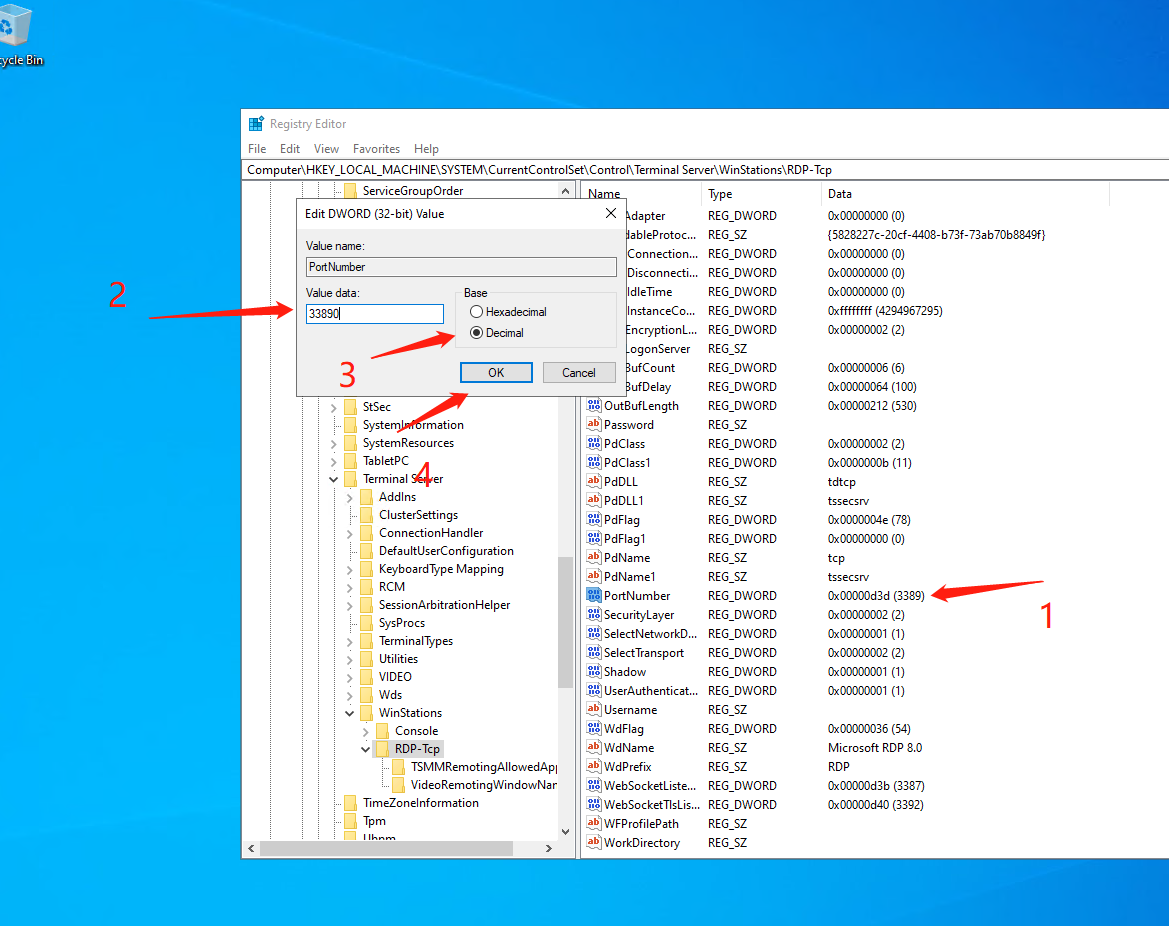
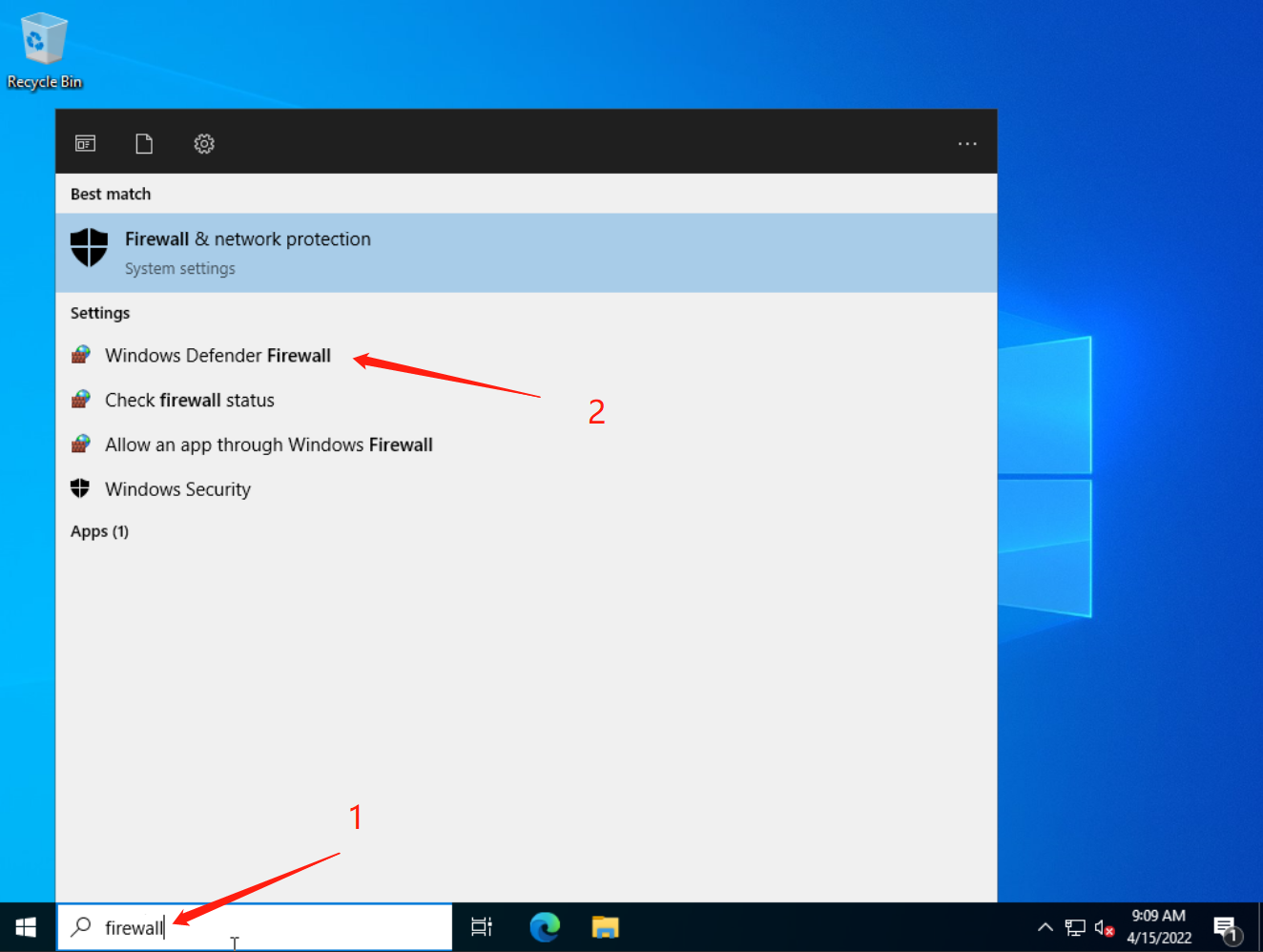
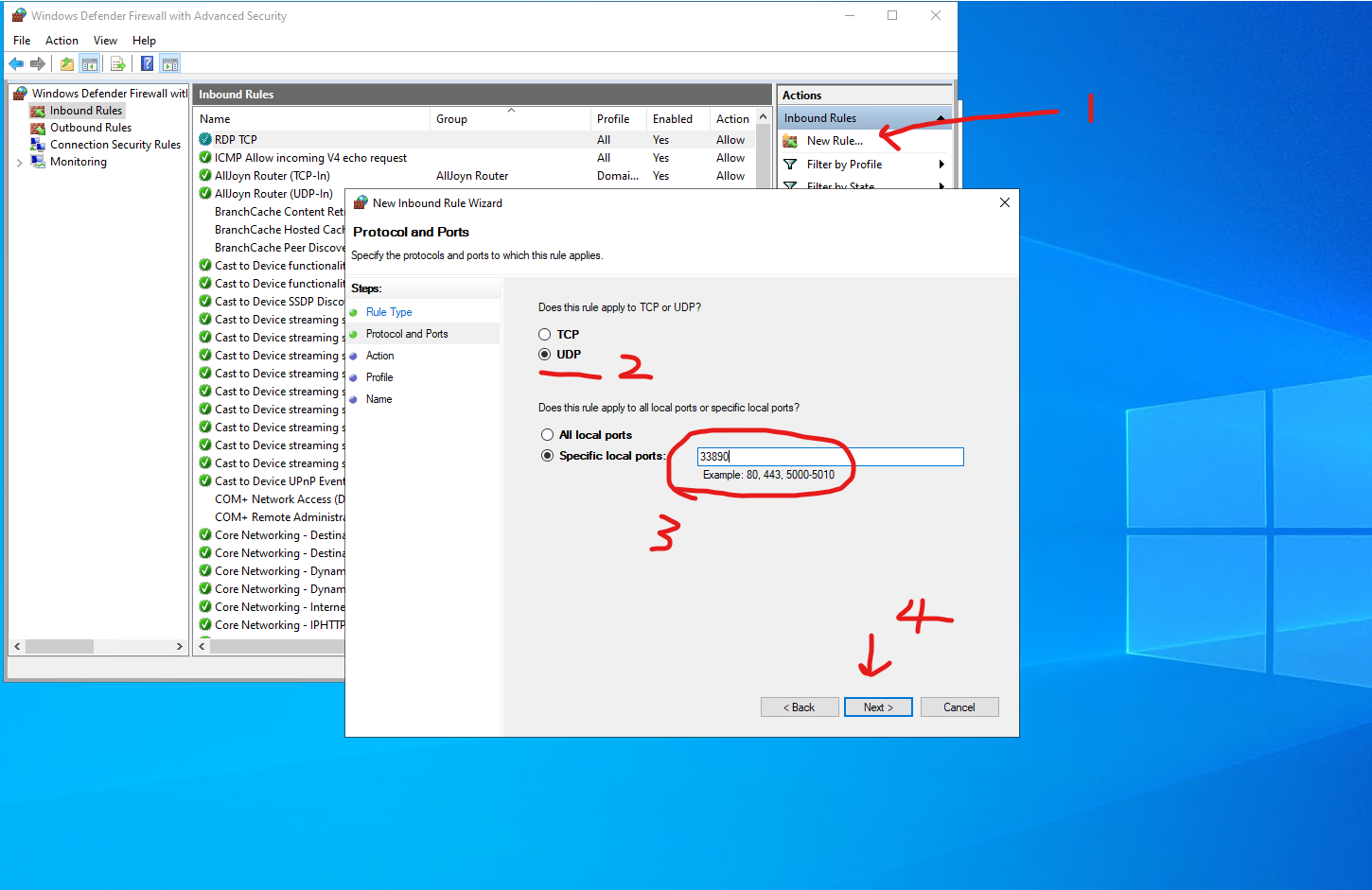
Before rebooting, don't forget to change the Firewall settings!
Search firewall in Windows Search. Go to the Windows Defender Firewall.
Go to Advanced settings:
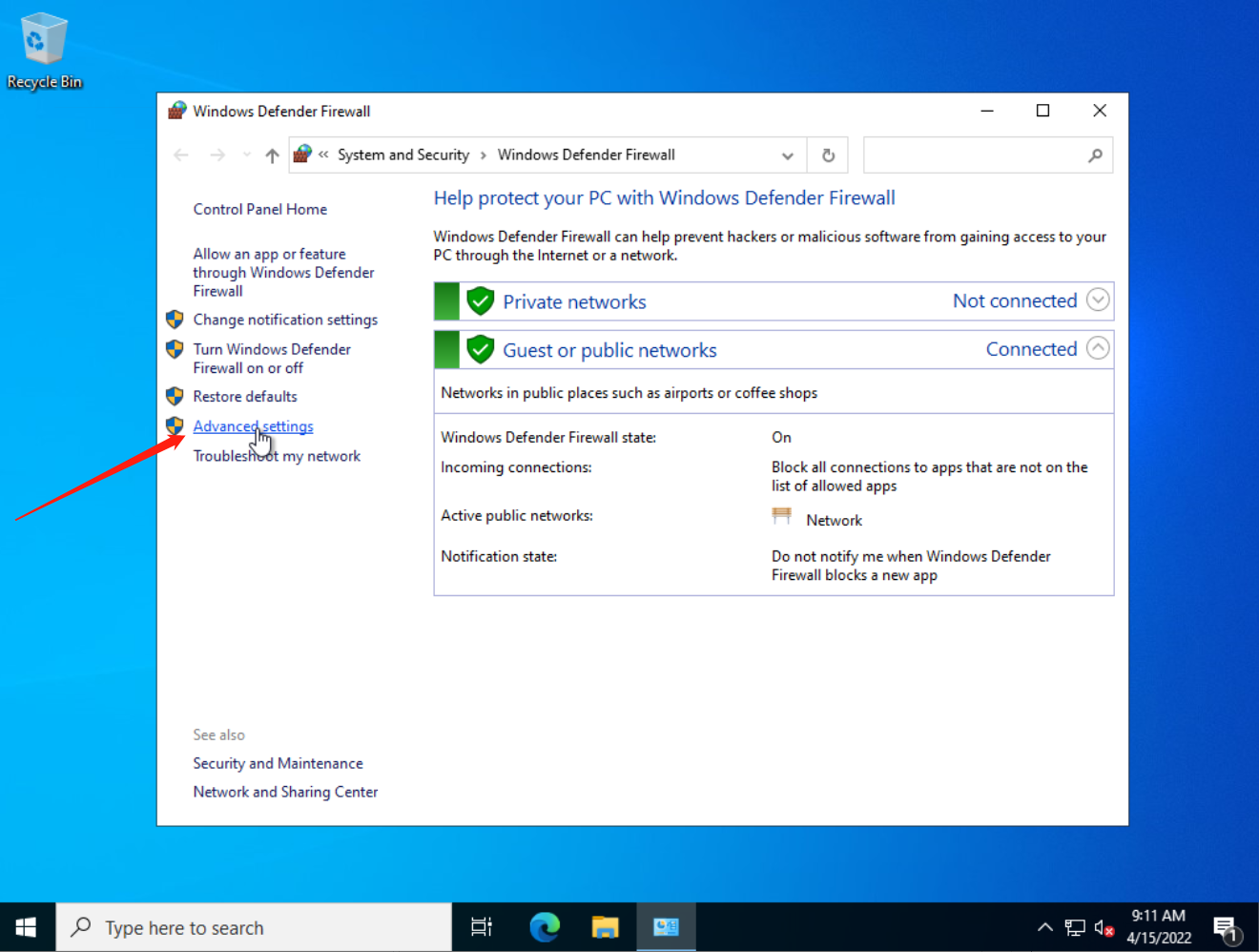
Go to the Inbound Rules. Add a new rule, select Port rule:
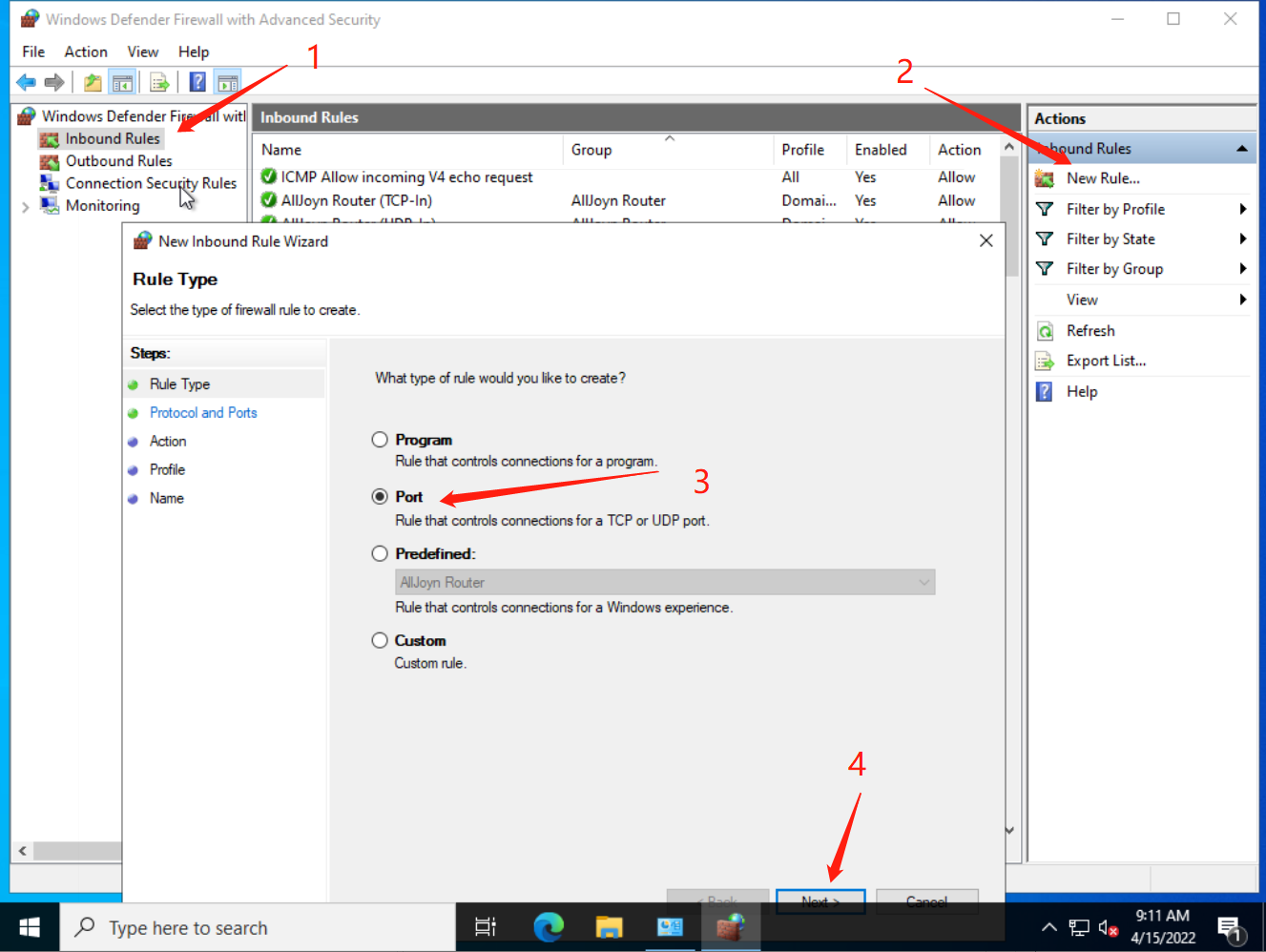
Input the port you set. First we gonna create a new TCP rule. You can then create a UDP rule later. This is optional.
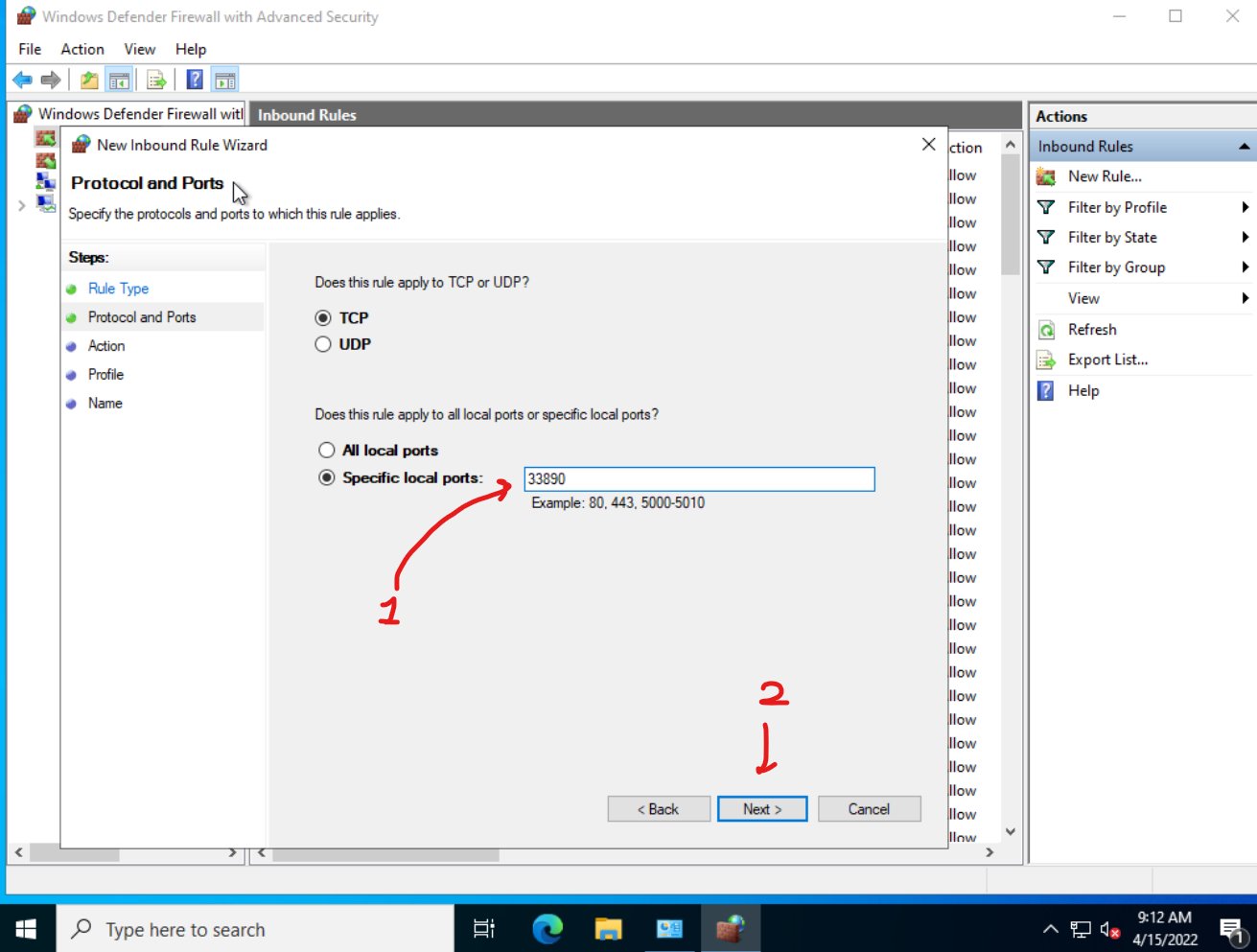
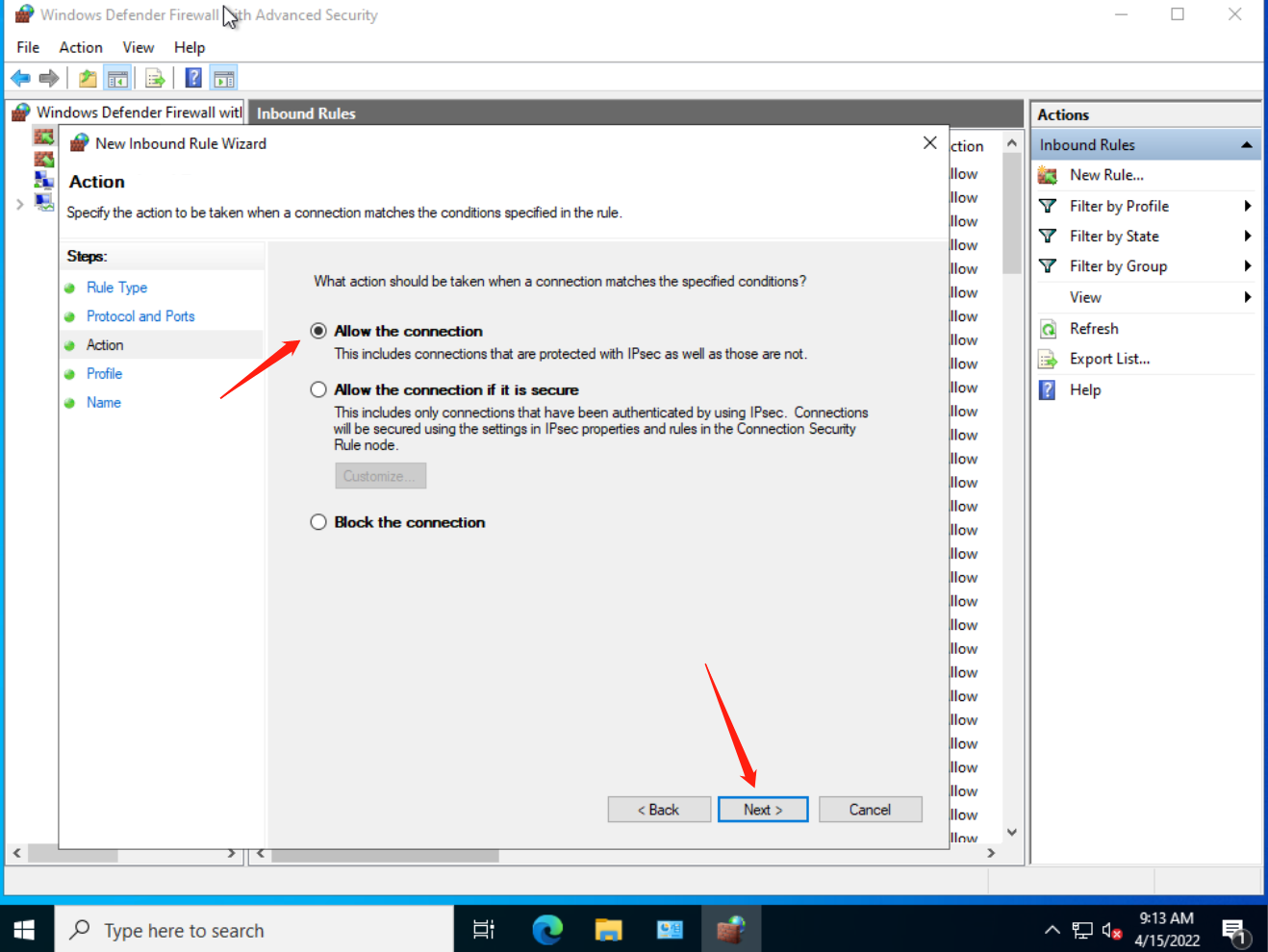
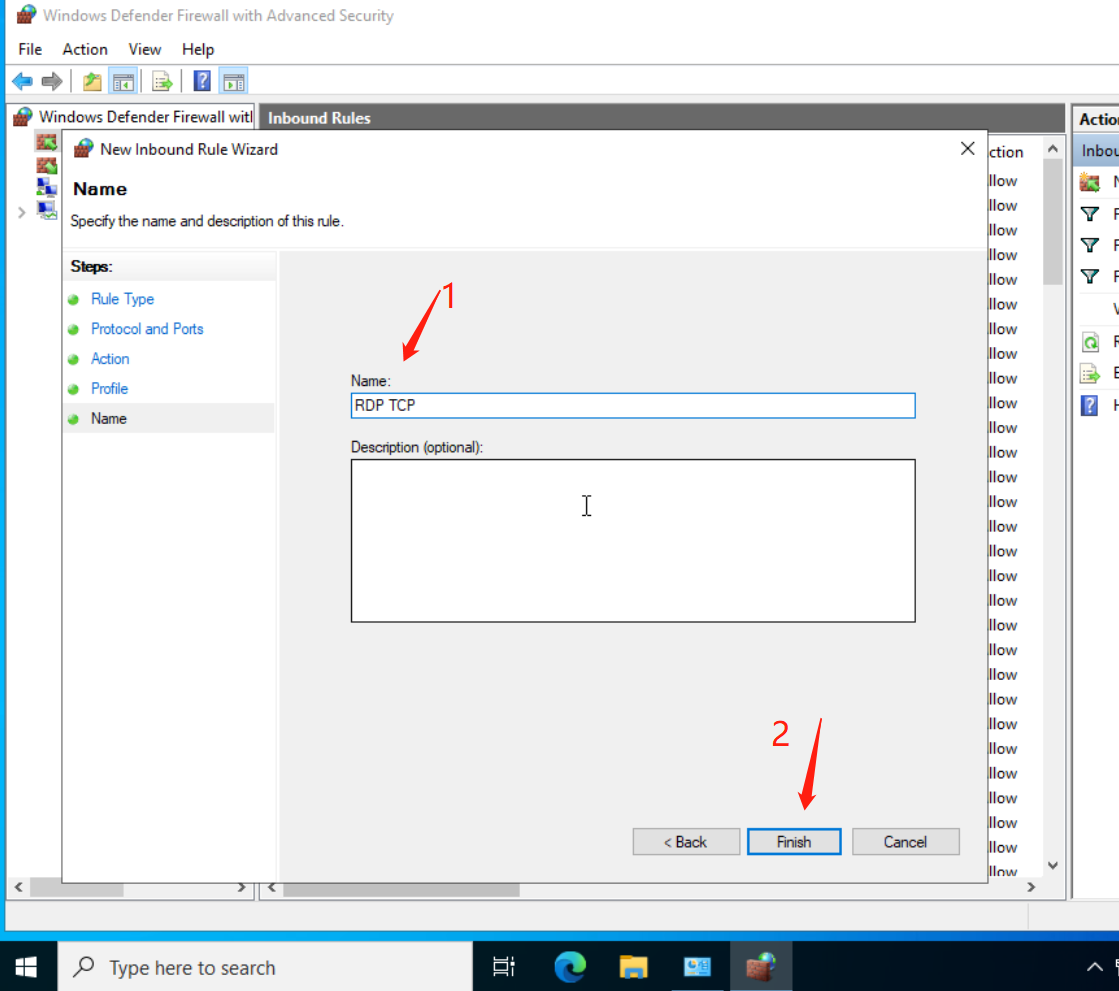
Then reboot the machine.
After rebooting, connect with the new port:
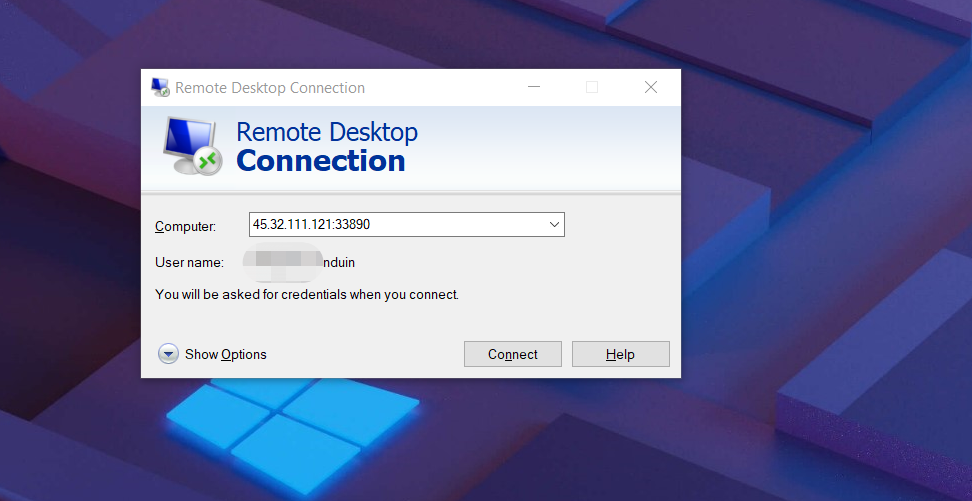
After connecting, you can create a new UDP rule.
After configuring those security settings, you can install some additional software suitable.
Strongly suggest installing the following tools on your new Windows Server.
- IIS Crypto to change IIS settings to best practice.
- CPUZ to benchmark CPU performance.
- WinDirStat to analyse disk usage.
- NSSM to manage background services
- FRP to expose the IP address to public internet when your server is behind NAT or firewall.
- 7zip to manage zip files.
- FastCopy to backup\migrate\copy server files faster and easier.
- Win-ACME to enable TLS encryption for Windows Server.
- Visual Studio Code to edit configuration files easier.
- AdoptOpenJDK to run Java programs.
- .NET Windows Server hosting bundle to support running ASP.NET Core applications.
- Git and Git-Bash to use version control and run bash scripts
- Aria2 to speed up the download speed of Windows Server.
- Winget and Windows Terminal to manage packages
您的文章为Windows Server安全配置提供了非常实用的指南,内容结构清晰,操作步骤详实,对新手和有经验的运维人员都具有参考价值。以下是对文章的深度分析与改进建议:
优点与核心理念赞赏
可改进空间与专业建议
端口变更的局限性补充
账户管理的冗余性考量
net localgroup Administrators命令验证),避免因误操作导致管理权限中断工具推荐的深度延伸
安全策略的完整性建议
技术细节补充建议
RDP端口变更的隐藏风险
netstat -ano | findstr :<port>)IIS协议禁用的扩展说明
日志审计建议
总体而言,本文在Windows Server基础安全配置领域具有重要参考价值。若能补充上述专业细节,将更符合企业级安全运维标准。期待您后续对高级安全主题(如证书管理、自动化安全扫描)的深入探讨。
这篇文章详细介绍了如何为Windows Server进行安全配置,并推荐了多种实用工具来提升服务器的性能和安全性。以下是我对这些内容的一些思考和补充:
首先,关于用户权限管理,确保非管理员账户拥有最小必要的权限是关键。这不仅有助于防止误操作带来的风险,还能有效限制潜在攻击者的权限范围。在实际操作中,建议定期审核用户的权限,以适应组织结构或业务需求的变化。
其次,修改默认管理员密码并禁用默认帐户是非常重要的步骤,但别忘了配置账户锁定策略和复杂的密码要求。通过设置账户锁定阈值和强制复杂密码,可以进一步提高服务器的安全性,防止暴力破解攻击。
在远程桌面服务(RDS)的配置中,使用非标准端口确实能有效避免自动化扫描工具的攻击。此外,启用网络级别身份验证(NLA)不仅提升了安全性,还能减少带宽消耗。对于连接日志的监控,建议集成到集中式安全信息和事件管理系统(SIEM),以便及时发现异常行为。
防火墙配置方面,除了允许必要的端口外,还应定期审查规则集,删除不再使用的规则。同时,可以考虑启用出站规则,默认拒绝所有出站流量,并仅允许已知的必要服务通过。这有助于防止恶意软件在突破入站防御后进行数据外传。
网络高级安全策略中的IPSec配置是一个强大的工具,但需要谨慎设计策略以免影响正常业务。建议先从小范围测试开始,确保规则不会导致合法通信中断。此外,可以考虑使用基于证书的认证机制,进一步增强连接的安全性。
在安装额外软件时,选择开源和社区支持好的工具通常更可靠。例如,除了IIS Crypto,还可以考虑使用OpenSSL来管理服务器证书,或者使用Fail2Ban这样的工具来监控和封锁频繁尝试登录失败的IP地址。对于开发环境,配置自动构建和测试流水线(CI/CD)也是提升效率的好方法。
最后,定期进行安全审计和渗透测试是保持服务器安全性的重要环节。通过模拟攻击者的视角发现潜在漏洞,并及时修复,可以确保服务器始终处于较高的安全水平。同时,保持软件和系统补丁的更新,也是防止已知漏洞被利用的关键措施。
总的来说,这篇文章为Windows Server的新手提供了一个全面的安全配置指南。结合实际应用中的具体需求,进一步优化和扩展这些配置,将有助于打造一个既安全又高效的服务器环境。
In this blog post, the author provides a comprehensive guide on best practices after installing Windows Server, with a focus on security and efficiency. The core idea is to avoid using the default 'Administrator' user and instead create a new user with administrator privileges. This helps to enhance security by reducing the chances of unauthorized access. The author also suggests changing the default RDP port to reduce the risk of brute force attacks.
The blog post is well-structured, with clear step-by-step instructions and relevant screenshots to guide readers through the process. The author also provides a list of recommended tools and software for various purposes such as IIS Crypto for IIS settings, CPUZ for CPU performance benchmarking, and WinDirStat for disk usage analysis, among others.
One of the strengths of this article is its focus on security and the detailed explanations for each step. The author not only explains what to do but also why it is essential, which helps readers understand the reasoning behind each action.
However, there are a few areas where the blog post could be improved. For instance, it would be helpful to provide more context on why certain tools are recommended and how they can benefit the user. Additionally, the author could include some information on potential drawbacks or risks associated with certain steps, such as disabling the default Administrator user, to help readers make informed decisions.
Overall, this blog post is a valuable resource for anyone looking to enhance the security and efficiency of their Windows Server installation. The author's attention to detail and focus on best practices make it a useful guide for both beginners and experienced users alike.
求第二张图片中的壁纸。
Very good!