Sometimes, we need to provide key-values as environment variables for Azure app service, like database connection strings.
In some cases, we might need someone to collaborate managing the app service. However, with app service environment variables access, he will also be able to connect to the database manually and do custom database operations, like drop database. That is not what we expected.
So how can we allow a person to manage our app service without touching the secret values? Here comes Azure Key vault.

Azure Key vault is a tool that:
Safeguard cryptographic keys and other secrets used by cloud apps and services
Before getting started, we need to create a new Azure Key vault. Select Azure Key vaults and click the Add button.
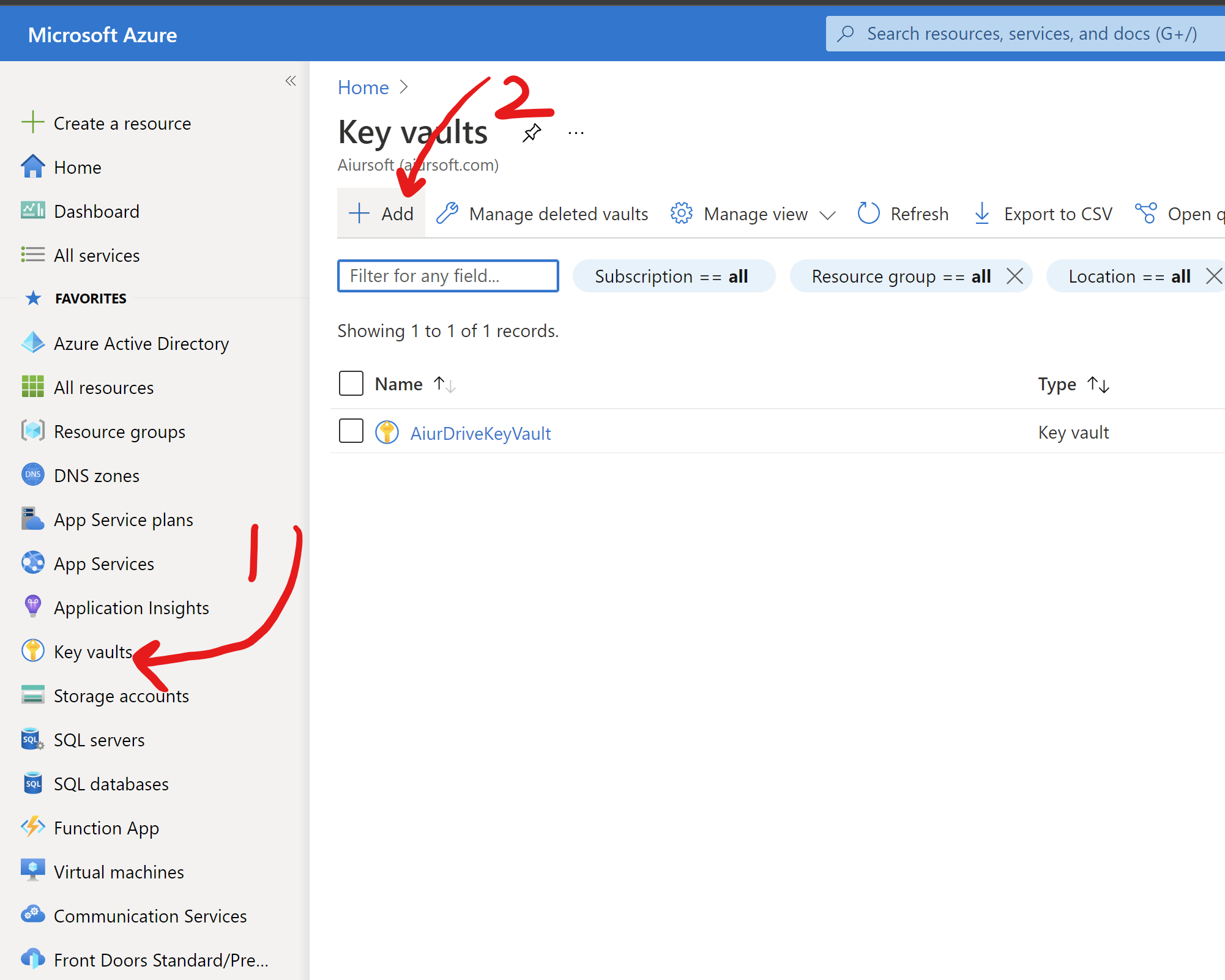
Fill in the form to select the subscription\resource group\region of your new Key vault. I suggest that you create a key vault in the region new your Azure App Service.
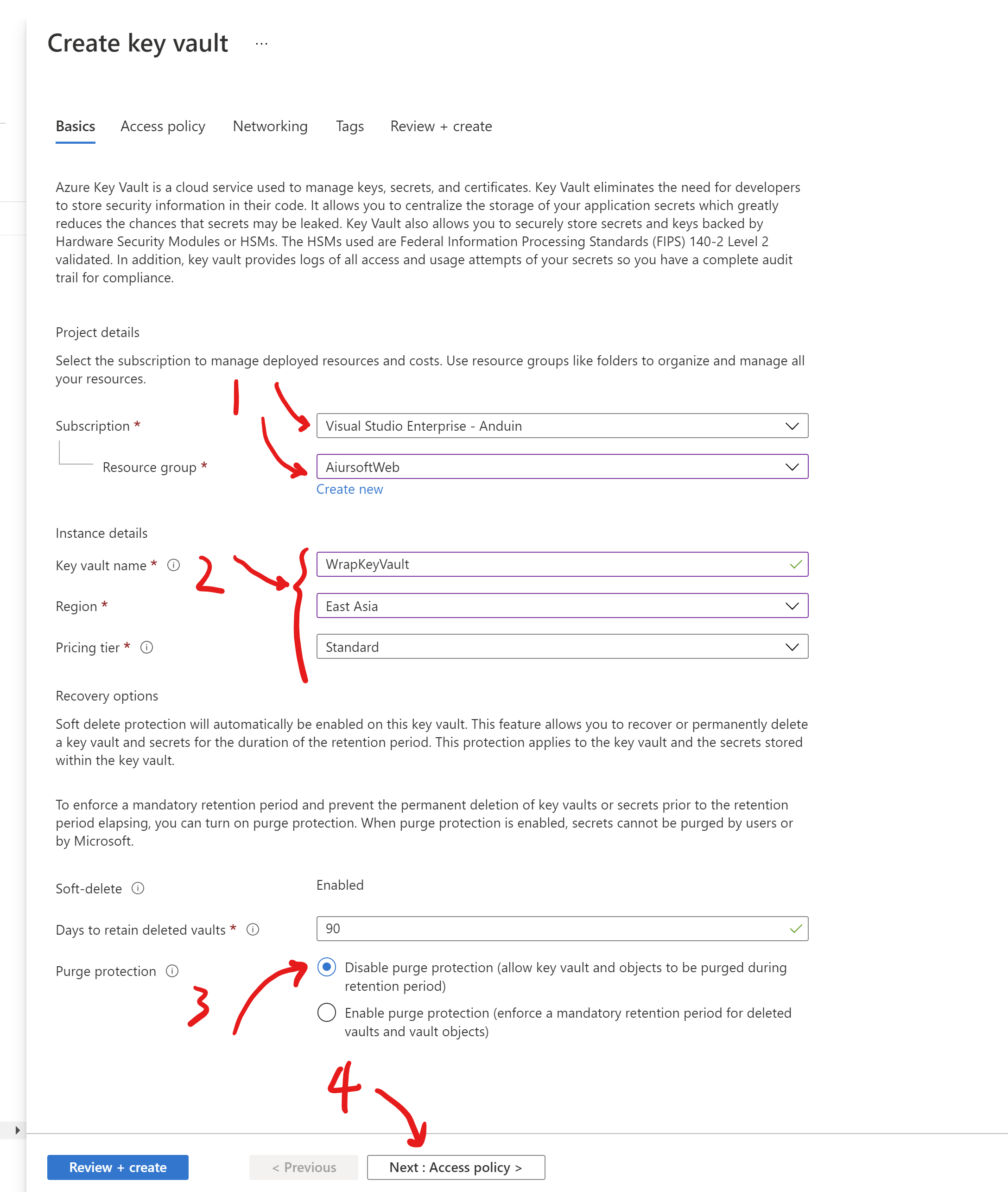
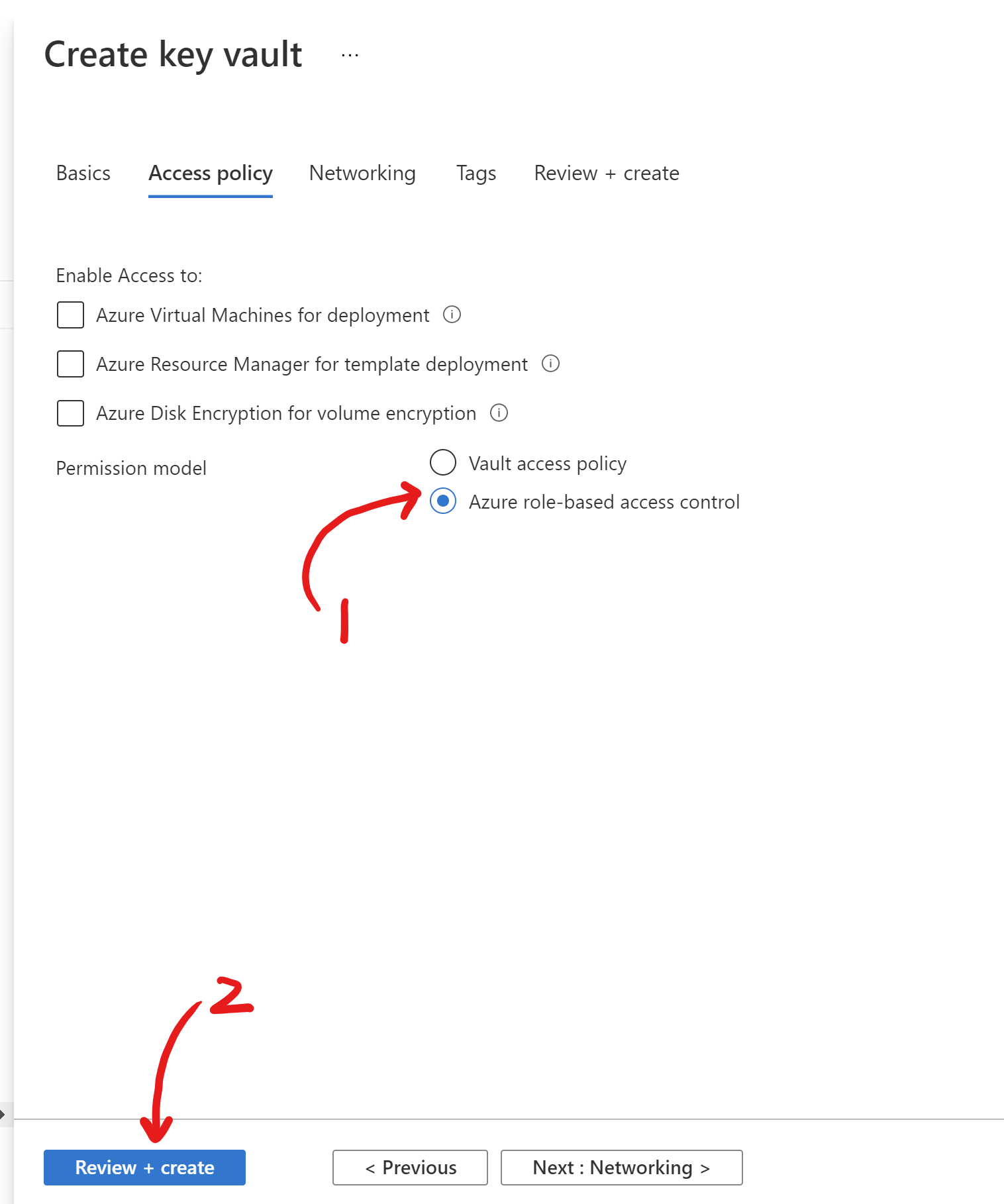
In the access policy part, select Azure role-based access control.
After clicking the create button, you need to wait for several minutes before the new Key vault is created.
After creating the new Key vault, you need to add yourself as the key admin which means that you can view\edit existing keys. It was not added by default for security reasons.
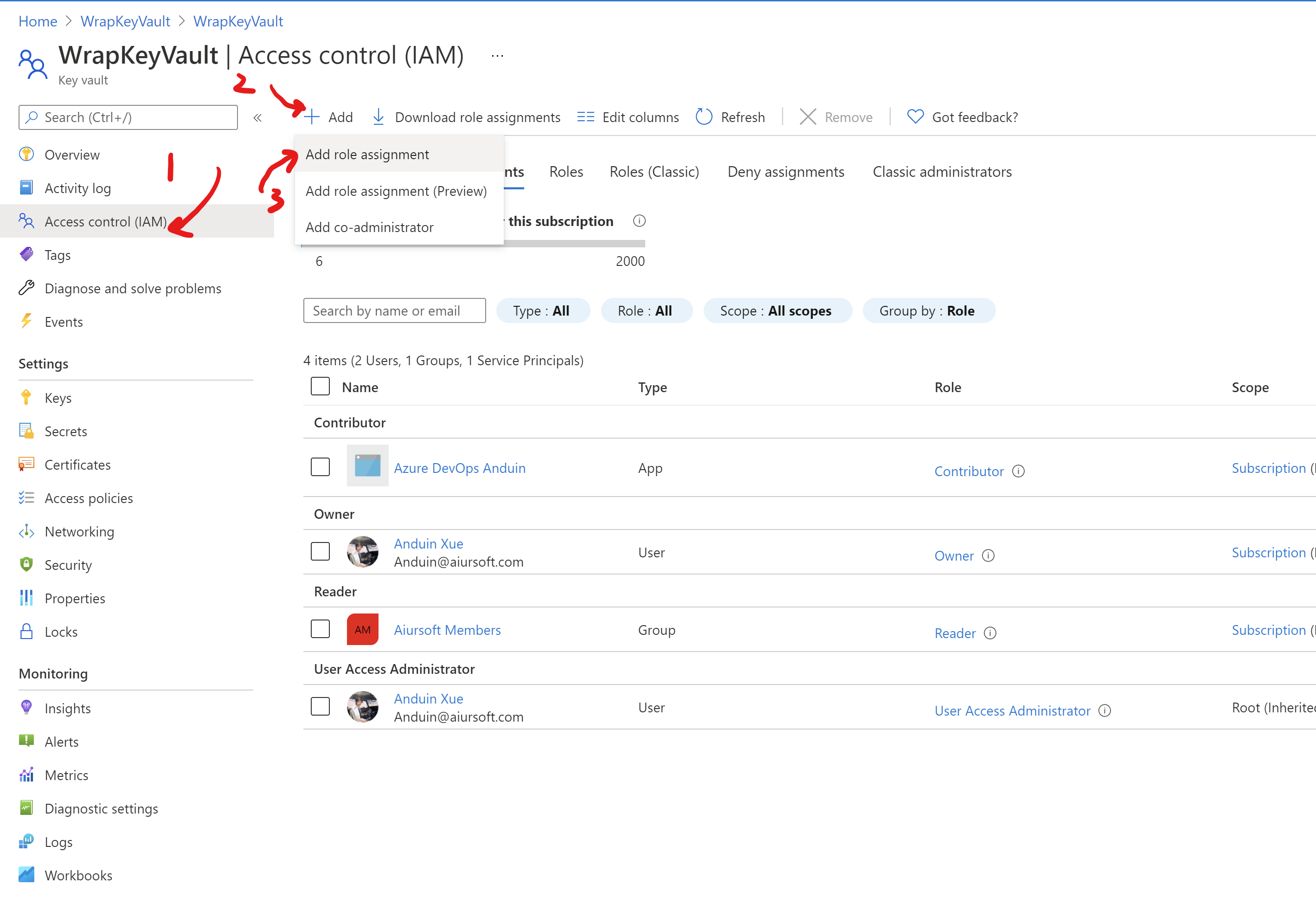
Select yourself to be added as Key Vault administrator.

Now, you can put the production connection string to the keys part:
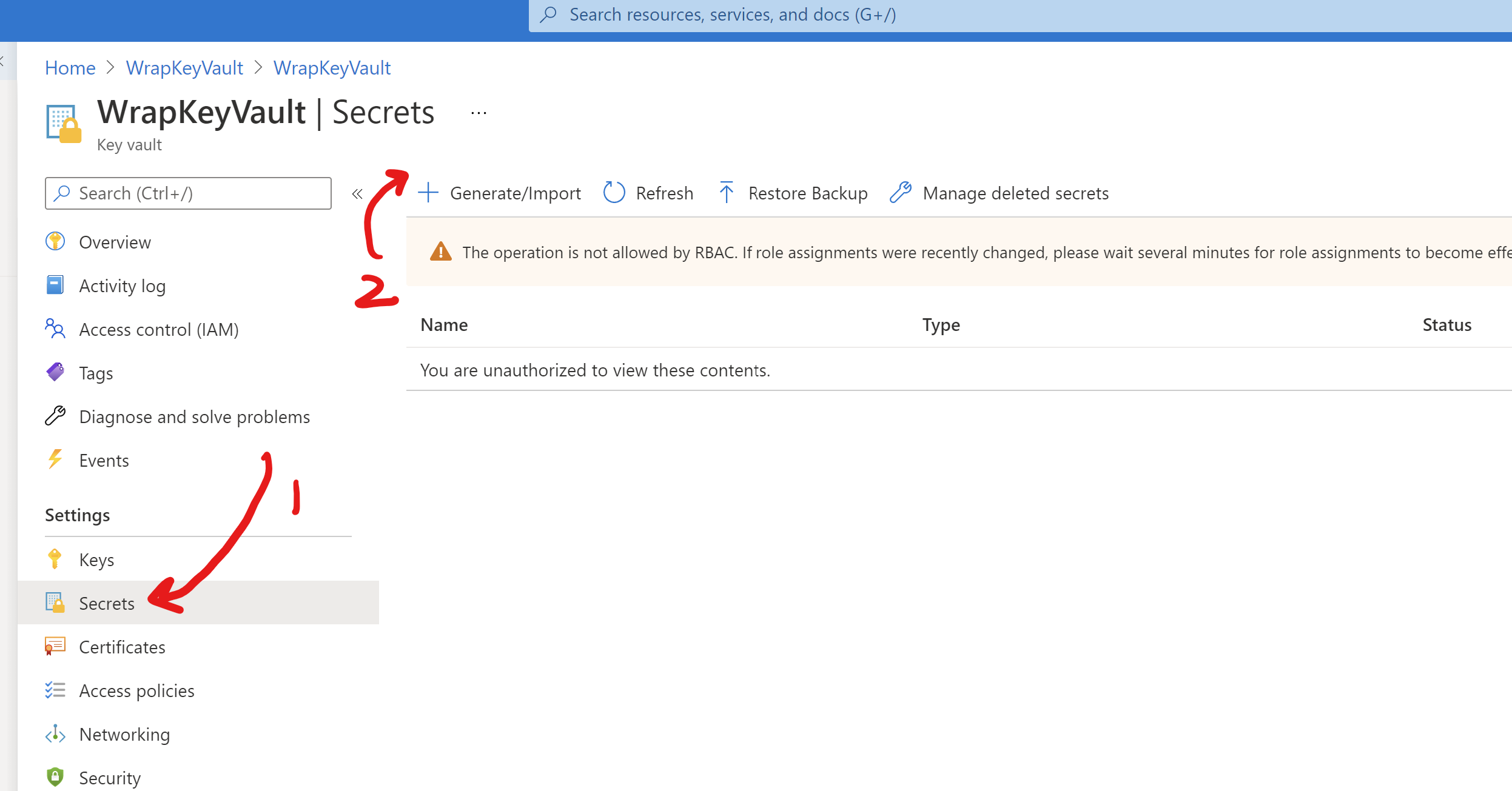

After creating the secret, copy the reference URL of it: (You can remove the version GUID in the last)
Example: https://wrapkeyvault.vault.azure.net/secrets/WrapDatabaseConnectionString

Wrap that to @Microsoft.KeyVault(SecretUri=xxxxx-the-url-you-copied)
And after wrapping, your link gonna be like this:
@Microsoft.KeyVault(SecretUri=https://wrapkeyvault.vault.azure.net/secrets/WrapDatabaseConnectionString)
And you paste that to your app service:
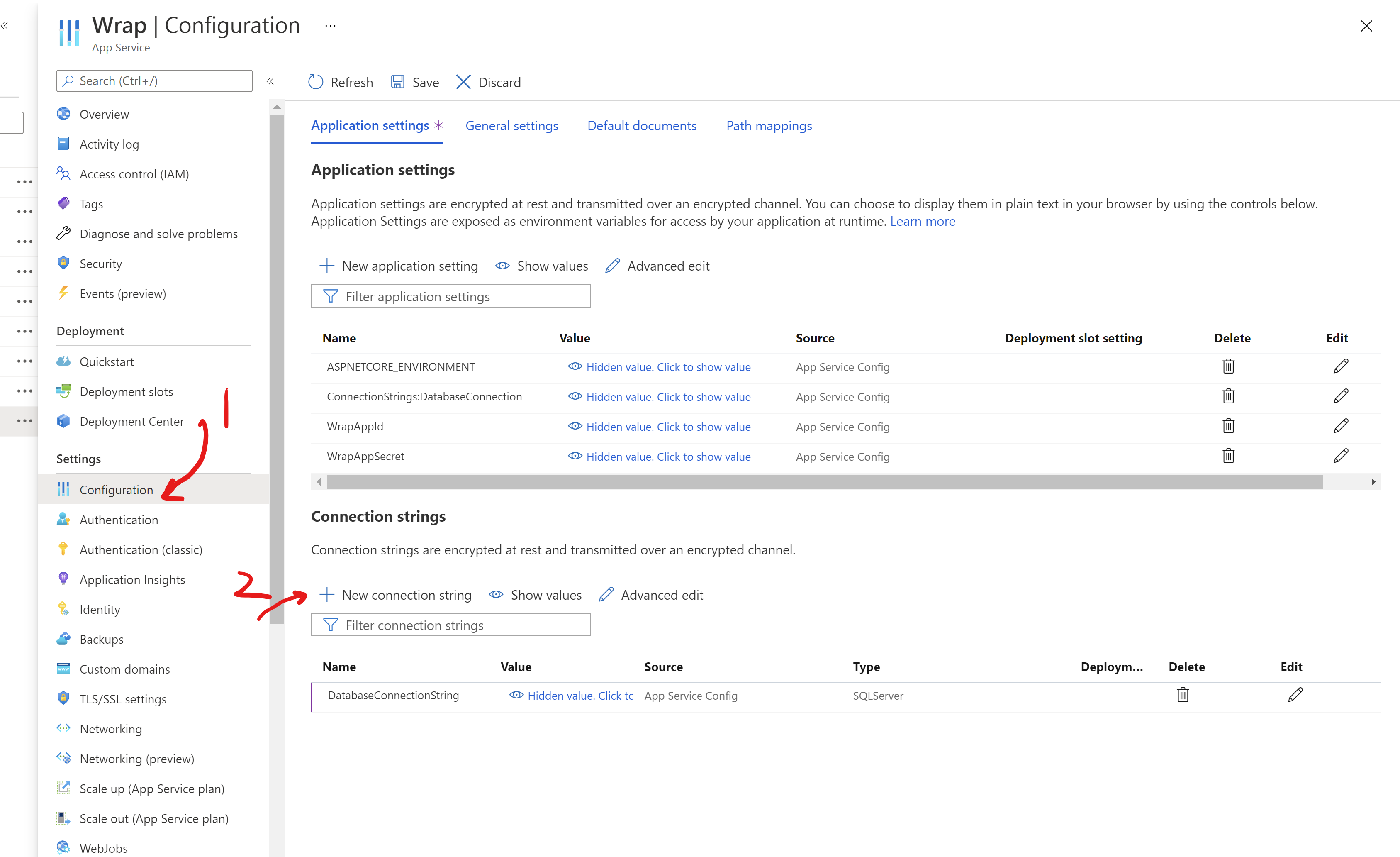
Paste the key vault reference instead of the real password like this:
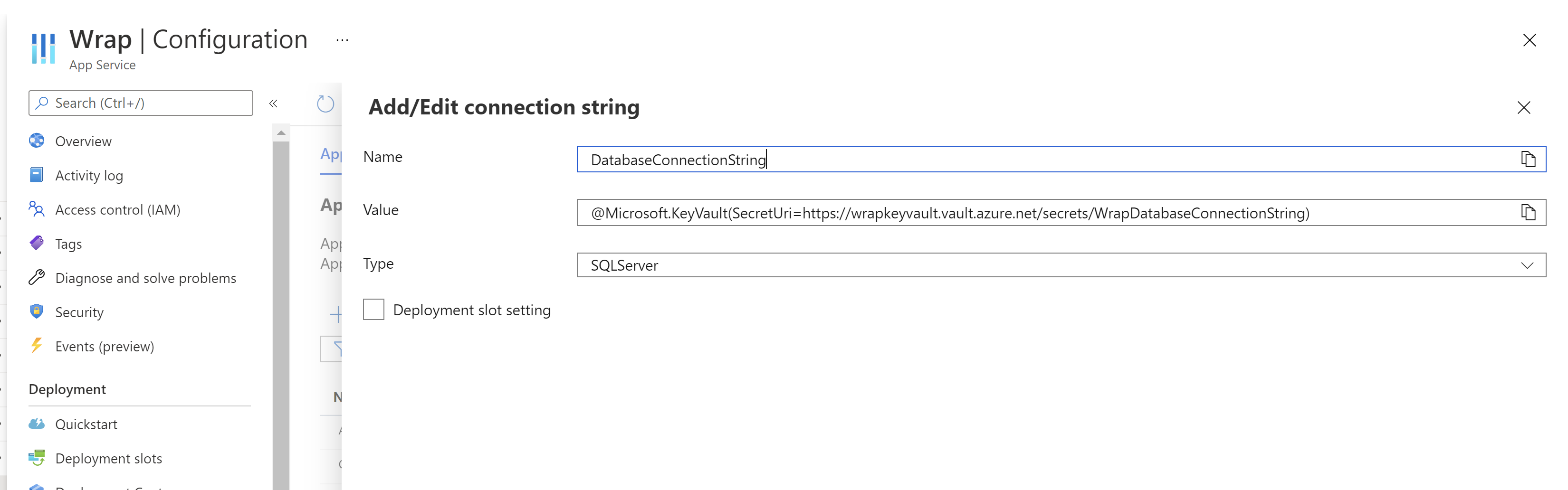
After saving the new value, restart the app service.
Now, we need to add an identity to allow the app service to access the key vault. First enable this switch:

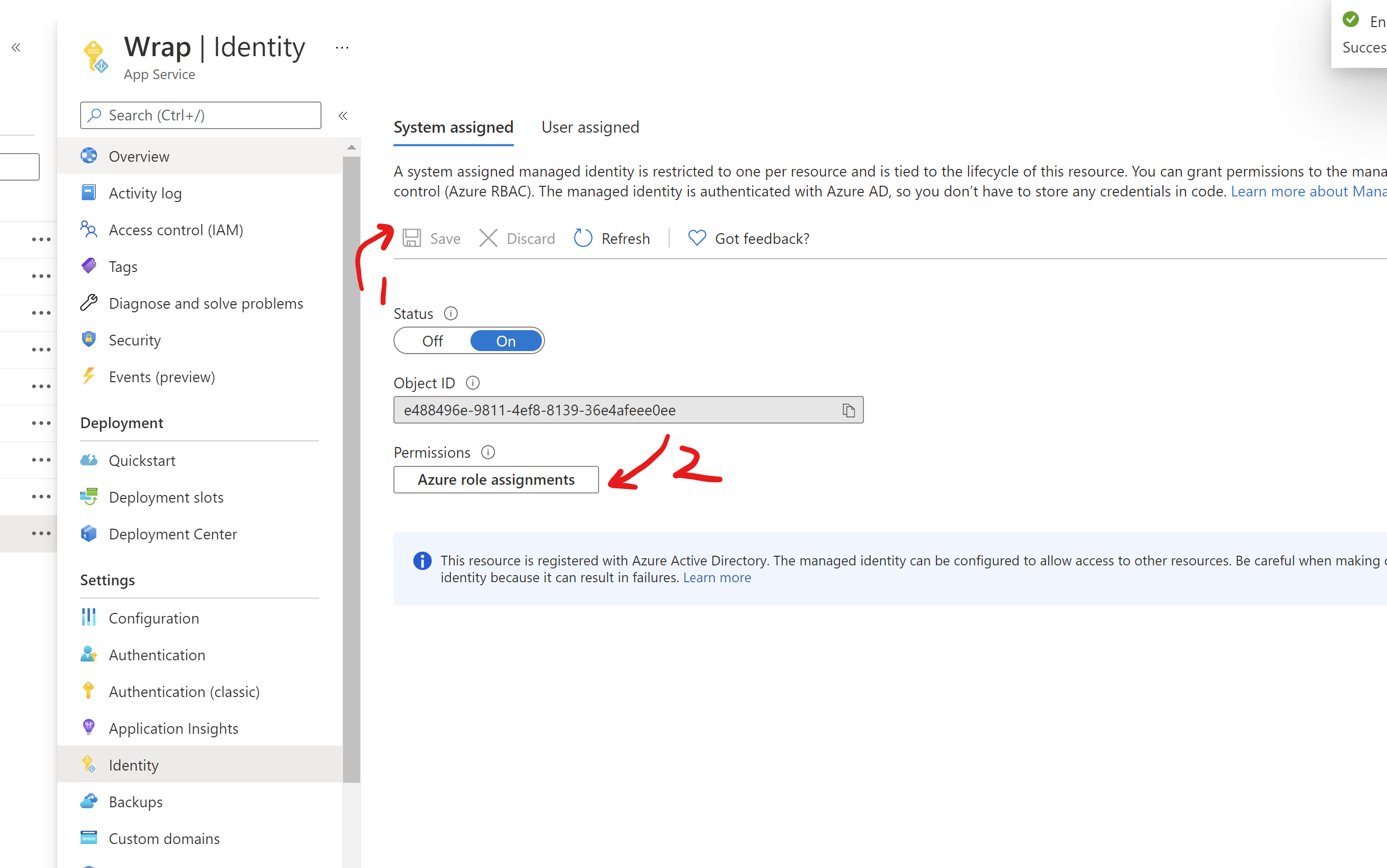
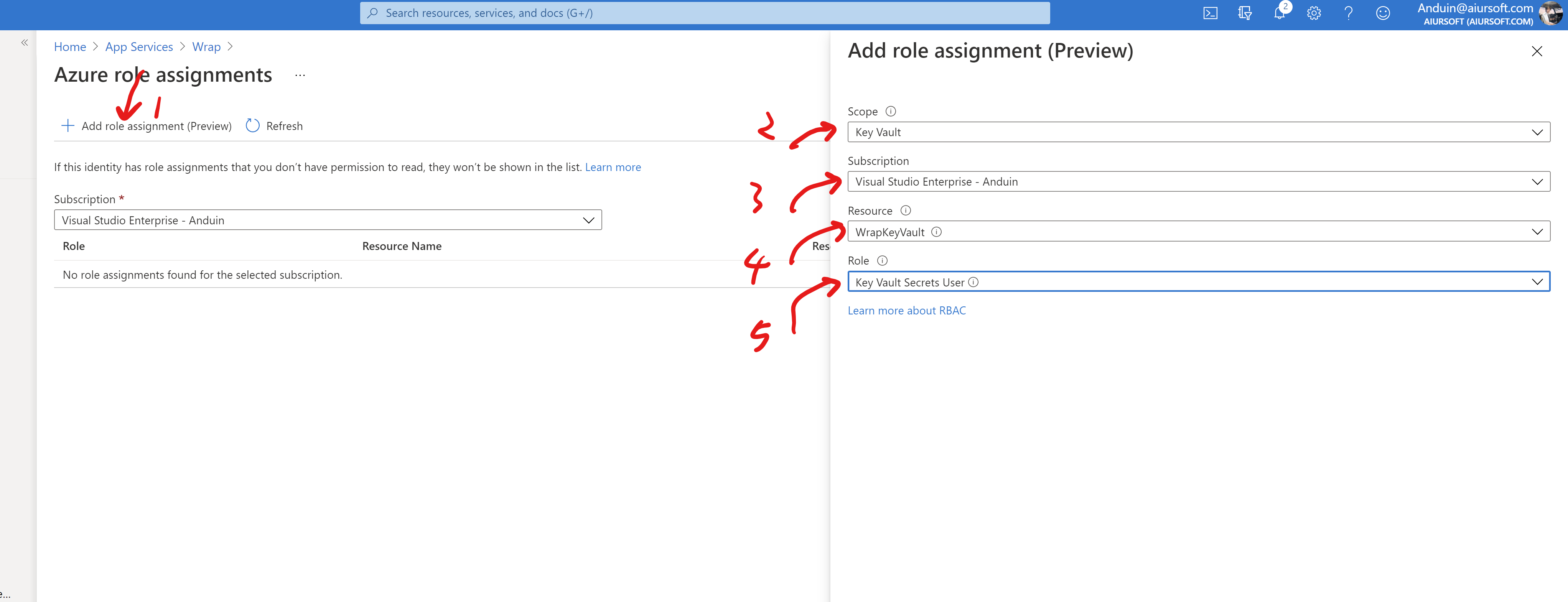
Select the key vault you need to access. Assign it as Key Vault Secrets User.
Finally, restart the app service. And test if it is still working.
Now, you can manage this service easily and without touching the confidential values. And the program can keep reading the value from the secure place.
You can also invite others to help you manage it without telling them the password of the database.
Enjoy coding!
本文系统性地演示了如何通过Azure Key Vault提升App Service连接字符串的安全性,体现了对云原生安全实践的深刻理解。文章最大的亮点在于通过"密钥引用"机制实现了权限最小化原则,既保障了数据库连接凭证的安全性,又保留了协同开发的灵活性。这种"环境变量+密钥服务"的组合方案,完美诠释了现代云应用对敏感信息的处理范式。
在技术实现层面,作者采用"问题-方案-步骤"的递进结构,通过12个图文结合的操作步骤,清晰展示了从Key Vault创建到权限配置的完整流程。特别值得肯定的是对"托管身份"的强调,这解决了传统环境变量配置中权限过度授予的痛点。截图标注的精准性(如标注"SecretUri"的格式要求)有效降低了读者实践的门槛。
建议在后续版本中补充以下内容:
目前存在两个可优化点:
文章对"密钥引用"语法的解析稍显简略,可考虑补充该语法的底层工作原理(如解析过程中的身份验证机制)。此外,关于密钥轮换策略的讨论将使安全方案更完整。总体而言,这是一篇极具实践价值的技术指南,期待看到更多关于Azure安全服务的深入解析。
你的博客详细介绍了如何使用 Azure Key Vault 来安全地存储和管理 Azure App Service 的连接字符串和其他敏感信息。这篇文章非常实用,特别是对于那些刚开始接触 Azure 安全工具的新手来说,它提供了一个清晰且易于跟随的指南。
优点:
改进建议:
解释关键决策:
访问策略详细说明:
解释关键操作:
@Microsoft.KeyVault参考的原因和机制,帮助读者理解 Azure 如何解析这些引用以及它们如何确保密钥的安全性。测试和验证:
进一步资源:
总结:
这篇文章已经是一份非常有价值的资源,但通过添加更多的背景信息、解释和扩展材料,可以帮助读者更深入地理解所涉及的概念,并增强他们的安全意识。继续保持这种清晰、实用的风格,未来可以考虑撰写更多关于 Azure 安全工具的文章,如 Azure Active Directory 的高级用法、自动化密钥轮换或其他安全最佳实践。
The blog post provides a detailed explanation of how to use Azure Key Vault to store connection strings for App Service, which helps in safeguarding cryptographic keys and other secrets used by cloud apps and services. The author presents a step-by-step guide on creating a new Azure Key Vault, adding oneself as the key admin, creating the secret, and pasting the key vault reference to the app service. This process allows for easier management of the service without exposing confidential values, and it enables collaboration without sharing sensitive information like database passwords.
The blog post's core idea of utilizing Azure Key Vault for secure management of connection strings in App Service is commendable. The step-by-step guide, along with the screenshots, make it easy for readers to follow and implement the solution. The author has done an excellent job of explaining the process in a clear and concise manner.
One area of improvement could be to provide a brief introduction to Azure Key Vault and its benefits at the beginning of the post. This would help readers understand the value of using Azure Key Vault before diving into the implementation steps.
Additionally, the author could also mention any potential limitations or considerations to keep in mind while using Azure Key Vault, such as the impact on performance, any additional costs, or other factors that may affect the decision to use this service.
Overall, the blog post is well-written and informative. The author has successfully demonstrated how to use Azure Key Vault for securely managing connection strings in App Service, which can be beneficial for readers looking for a secure solution for their cloud apps and services. Keep up the good work!